.png)
A cybersecurity audit is a systematic examination of an organization's security posture to identify and assess its vulnerabilities. Audits can be conducted for a variety of reasons, such as to ensure compliance with regulations, to identify areas for improvement, or to mitigate risk.
Cybersecurity audits are essential for businesses of all sizes, as they can help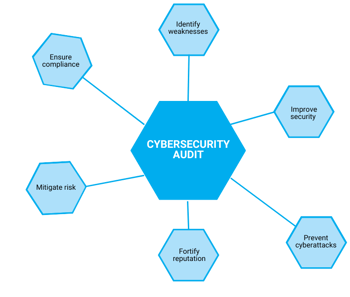 to protect sensitive data, prevent cyberattacks, and improve overall security posture.
to protect sensitive data, prevent cyberattacks, and improve overall security posture.
Why Are Cybersecurity Audits Necessary?
There are many reasons why cybersecurity audits are necessary for businesses. Let's dive in to some of the most common use cases for businesses.
Compliance with regulations
Many industries are subject to regulations that require them to undergo regular cybersecurity audits. For example, manufacturing companies with government contracts are required to have cybersecurity audits in compliance with CMMC. This ensures the extremely sensitive government information is kept out of the wrong hands. However, CMMC level 1 contractors are only required to self-assess for their audit, because the contracts they serve are considered not sensitive or critical to national security. CMMC Levels 2 and 3, on the other hand, require third-party assessors as the information in their contracts is deemed critical to national security. This is just one compliance example where cybersecurity audits are absolutely necessary, but it shows the overarching idea behind audits in general: ensuring the organization is mature enough cybersecurity-wise to protect data.
kept out of the wrong hands. However, CMMC level 1 contractors are only required to self-assess for their audit, because the contracts they serve are considered not sensitive or critical to national security. CMMC Levels 2 and 3, on the other hand, require third-party assessors as the information in their contracts is deemed critical to national security. This is just one compliance example where cybersecurity audits are absolutely necessary, but it shows the overarching idea behind audits in general: ensuring the organization is mature enough cybersecurity-wise to protect data.
Identification of vulnerabilities
Organizations that are proactive about their cybersecurity investments and implementations are always looking to identify areas for improvement. For those organizations that don't know, cybersecurity audits play a crucial role in helping to uncover vulnerabilities within a security posture, enabling them to take those proactive measures to enhance their overall security. By identifying these weaknesses, organizations can implement effective corrective measures that bolster their defense against potential cyber threats.
Mitigation of risk
Going hand-in-hand with our last point above, by conducting cybersecurity audits, businesses can effectively minimize the potential risks and threats posed by cyberattacks. Risk management is an extremely important part of having a strong cybersecurity posture. Identifying and prioritizing your risks helps to keep your organization on the fast track to fully secure. Through the identification and resolution of vulnerabilities, organizations can significantly enhance the security of their systems and data, making it increasingly challenging for attackers to breach their defenses.
Improvement of security posture
Through the implementation of cybersecurity audits, businesses can proactively strengthen their defense against potential cyber threats and bolster their overall security posture. One of the most universal and structured way to do this, is by following the NIST Cybersecurity Framework (CSF). The NIST CSF is recognized worldwide as cybersecurity best practices that anyone can follow. Many regulatory framework are based on the CSF, and pull best practices from it to implement to their own frameworks. By conducting cybersecurity audits, organizations gain valuable insights into areas that require improvement and can take effective corrective measures to ensure the utmost protection of their systems and data.
4 Steps to Prepare for a Successful Cybersecurity Audit
There are four main steps that businesses can take to prepare for a successful cybersecurity audit.
1. Understand the audit requirements.
To kickstart your cybersecurity audit, it's crucial to grasp the specific requirements of the assessment. These requirements are influenced by the industry you operate in, the applicable regulations, and the specific goals of the audit. For instance, like we mentioned earlier, government manufacturers must adhere to CMMC, necessitating the implementation of specific security controls to safeguard sensitive government information. Similarly, healthcare organizations must comply with HIPAA to ensure the privacy of patients' health information. The most effective way to comprehend the audit requirements is to carefully review the audit plan or request a copy directly from the auditor.
2. Assess your current security posture.
Once you gain a thorough understanding of the audit requirements, it is imperative to evaluate your current security posture. This entails identifying and safeguarding your valuable assets, such as your computer systems, networks, and crucial data. Additionally, it is crucial to recognize the potential threats that could pose harm to your assets, including cyberattacks, natural disasters, and human error. Furthermore, it is essential to identify any weaknesses or vulnerabilities in your security posture that could potentially be exploited by these threats. To effectively assess your security posture, there are a plethora of tools and techniques available, ranging from vulnerability scanning and penetration testing to comprehensive risk assessments.
3. Implement corrective measures.
Once you have completed your assessment, it is crucial to take action and implement effective measures to address any vulnerabilities that were identified. This may involve updating your existing security policies and procedures, introducing new security controls, or providing training to your employees. It is essential to prioritize the most critical vulnerabilities and ensure that the corrective measures are not only effective but also properly implemented. By doing so, you can enhance your overall security posture and strengthen your organization's resilience against potential cyber threats.
4. Document your findings.
After implementing the necessary corrective measures, it is crucial to meticulously document your findings. This documentation will not only provide the auditor with a comprehensive understanding of your organization's security posture but also enable them to identify any areas that require improvement. Make sure to include a detailed description of your valuable assets, potential threats, vulnerabilities, and the specific corrective measures taken. Additionally, it is essential to include the results of any testing or assessments conducted as part of the cybersecurity audit process. By documenting your findings thoroughly, you can demonstrate your commitment to maintaining a robust security program and continuously improving your overall security posture.
meticulously document your findings. This documentation will not only provide the auditor with a comprehensive understanding of your organization's security posture but also enable them to identify any areas that require improvement. Make sure to include a detailed description of your valuable assets, potential threats, vulnerabilities, and the specific corrective measures taken. Additionally, it is essential to include the results of any testing or assessments conducted as part of the cybersecurity audit process. By documenting your findings thoroughly, you can demonstrate your commitment to maintaining a robust security program and continuously improving your overall security posture.
Final Thoughts
Cybersecurity audits are an important part of any organization's security program. By following the four steps outlined above, businesses can prepare for a successful audit and improve their overall security posture.
At Charles IT, we know that audit preparation takes a lot of time, effort, and resources. We also know that it's important to take as little time as possible away from your business and your mission. That's why we're here to help! If you'd like advice or assistance on how to get your cybersecurity posture audit-ready, reach out to us today to see how we can be of assistance.




