
In our previous blog, we discussed that one of the key differences between Defense Federal Acquisition Regulation Supplement (DFARS) and Cybersecurity Maturity Model Certification (CMMC) is the latter’s three maturity levels.
In this blog, we’ll delve deeper into the focus and requirements of all three CMMC 2.0 certification levels.
|
Before proceeding, make sure to read this first: |
Overview: Three CMMC 2.0 Levels
The CMMC has the same goal as DFARS, which is to protect the controlled unclassified information (CUI) that Department of Defense (DoD) suppliers keep. Because of this, the CMMC operates on a framework that builds upon existing DFARS requirements. It consists of three levels that DoD suppliers mature into the better they get at protecting federal contract information (FCI) and CUI.
Particularly, each CMMC 2.0 maturity level is characterized by a set of cybersecurity processes and practices.
The CMMC 2.0 levels and their associated cybersecurity processes and practices are cumulative. This means that to be certified at a certain CMMC level, you must meet all of the requirements of the preceding levels as if you're applying for certifications for all of those levels. This allows applicants to apply for a certification level of their choosing once, rather than having to go through certifications multiple times.
Each CMMC 2.0 level also has a particular focus to ensure alignment between cybersecurity processes and practices with the type and sensitivity of information to be protected.
Now, let’s take a closer look at each CMMC 2.0 level.
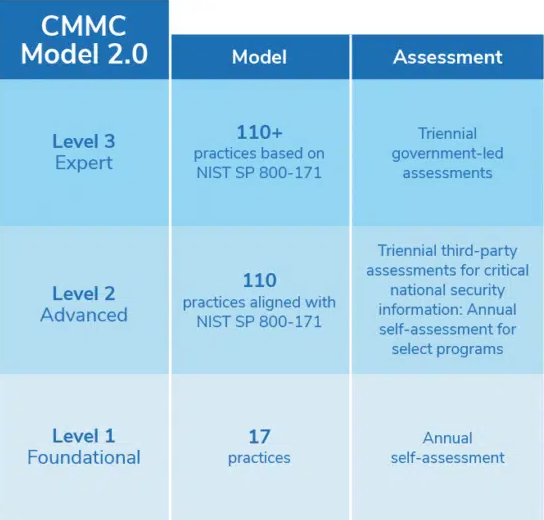
CMMC 2.0 Level 1: Foundational Cyber Maturity
Guided by the Federal Acquisition Regulation (FAR), this is the minimum level of cyber hygiene required to hold Federal Contract Information (FCI), beyond the DoD. A level 1 certification indicates that cybersecurity best practices concerning the identified controls are “performed” and included in the business’s processes.
This is the easiest of the three levels to achieve, and contractors may self-certify.
CMMC 2.0 Level 2: Advanced Cyber Maturity
Any company working with CUI should aim for this level. It is comparable to the former CMMC Level 3. These requirements are in complete alignment with NIST SP 800-171 practices. All practices and maturity processes that were unique to CMMC 1.0 have been eliminated, which means that the 20 requirements in the old CMMC Level 3 that the DoD had imposed were dropped. Now, Level 2 directly correlates with the 14 levels and 110 security controls developed by the National Institute of Technology and Standards (NIST) to protect CUI.
CMMC 2.0 Level 3: Expert Cyber Maturity
Contractors at this level are required to focus on reducing the risk from Advanced Persistent Threats (APTs). This level is exclusively for companies working with CUI on DoD’s highest priority programs. It is comparable to the old CMMC Level 5. The DoD has indicated that its requirements will be based on NIST SP 800-171’s 110 controls plus a subset of NIST SP 800-172 controls. These should be met before undergoing a triennial government-led assessment. The DoD, however, is in the process of developing the requirements for this level, which is still undergoing change.
As a DoD contractor, you should identify your organization’s cyber security level based on the classification of the data you store, transmit, and process. Your IT team must be familiar with NIST SP 800-171 and the appropriate target levels so that they can determine the right CMMC 2.0 controls to adopt for your organization.
Understanding how you can prepare the transition to CMMC 2.0 compliance is a must no matter what cyber security level you are aiming for. This is where experienced professionals can be a tremendous asset.
Wrap-Up
For a quick summary of the total number of practices and technical frameworks adopted by each CMMC level, refer to the diagram below.
Feeling overwhelmed by the technical complexity of meeting CMMC compliance? Don’t worry, Charles IT is here to help you using our two-step process: gap assessment + CMMC services. Get started today by uncovering your company’s security gaps.
Editor's Note: This blog was originally published on August 12, 2020. It was edited for accuracy on July 30, 2023.

.png)



