The US Department of Defense (DoD) supply chain is a prime target for cybercriminals and hostile nations looking to steal and expose sensitive government information. These threats led to the creation of the Defense Acquisition Federal Regulation Supplement (DFARS) in December 2015. DFARS is a set of cybersecurity standards designed to protect controlled unclassified information (CUI) from cyberthreats.
DFARS requires DoD contractors and subcontractors to comply with a set of security regulations or risk facing penalties and losing their contracts.
What is NIST 800-171?
NIST 800-171 is a set of guidelines and cybersecurity best practices designed to help DoD contractors improve their cybersecurity measures. It's divided into four core areas:
1. Functions
The NIST framework features six functions vital to managing cybersecurity risks. They are:
Govern -- Establish a strong governance framework to manage cybersecurity risks at the organizational level.
Identify – Identify cybersecurity risks to data, assets, and systems.
Protect – Create and implement safeguards to ensure critical infrastructure services are not disrupted.
Detect – Create and implement policies to detect cybersecurity anomalies and events.
Respond – Create and implement policies for containing potential cyberthreats.
Recover – Create and implement policies to restore services affected by a cybersecurity event.
2. Categories
Categories are specific tasks you must carry out for each of the six functions. For example, to protect your infrastructure from data breaches, you need to implement access control policies and install antivirus software.
3. Subcategories
Subcategories are tasks related to each category. For instance, if your category is updating all your software, your subcategory will be making sure that all your computers have the auto-update feature switched on.
4. Informative Sources
These are documents and policies that outline how specific tasks should be done. Take the example above. You should have available documents on how to enable auto-updates on your computers.
The CMMC 2.0 Framework: The Move to Third-Party Certification
The Cybersecurity Maturity Model Certification (CMMC) framework is a security standard that uses a three-level tiered system that determines the maturity of a DoD contractor based on its ability to protect sensitive government information from cyberattacks. Each level builds on each other's requirements. The three levels of the CMMC 2.0 framework are:
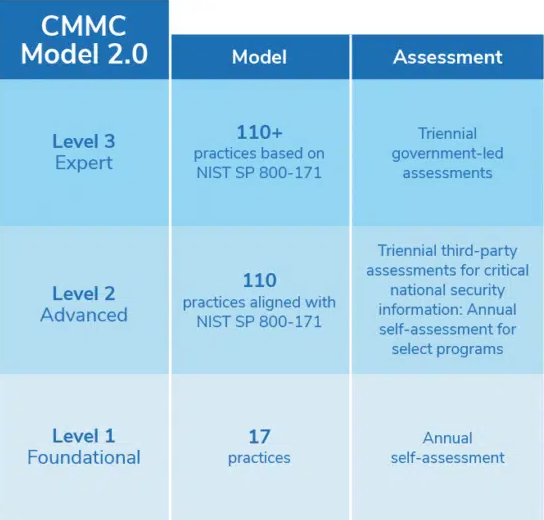
All DoD contractors and subcontractors must get a CMMC 2.0 certification before bidding for government contracts. And unlike DFARS, where self-certification is permitted, the CMMC 2.0 framework requires contractors to be audited by certified third-party assessor organizations (C3PAOs) accredited by the CMMC accreditation body. Having a third-party organization conduct the audit will ensure contractors applying for CMMC 2.0 certification meet all specified requirements.
NIST 800-171 vs. CMMC 2.0: Key Differences
CMMC 2.0 offers updated guidelines to help contractors and subcontractors meet the requirements found in NIST 800-171. However, some contractors are asking what's the difference between NIST 800-171 and CMMC. While both are designed to enhance the cybersecurity posture of contractors, there are key differences between NIST 800-171 and CMMC 2.0.
1. CMMC 2.0 Certification Requires Third-Party Assessment
Under NIST 800-171, contractors could self-certify and claim that their companies comply with all the NIST standards. Contractors applying for CMMC certification must first be audited by a C3PAO. This is to prevent false claims of compliance and ensure contractors applying for certification meet all CMMC requirements.
2. CMMC 2.0 Compliance Is Required to Win DoD Contracts
DoD contracts with CMMC requirements cannot be awarded to contractors and subcontractors who are not CMMC certified.
3. CMMC 2.0 Is Scalable
NIST 800-171 offers controls at only one level, with additional enhancements for extra protection. CMMC 2.0, on the other hand, uses specific levels of compliance, which contractors need to meet to be certified at a particular level. The three maturity levels used by the CMMC 2.0 framework allow contractors to scale their certification up or down depending on the security protocols they need.
4. CMMC 2.0 Focuses More on Cyberthreats
Both NIST 800-171 and CMMC 2.0 emphasize the need for audits, access control, configuration management, and personnel security. However, CMMC 2.0 also focuses on cyberthreat intelligence, cyberthreat alerts, and situational awareness. This helps contractors develop more efficient security protocols for identifying and managing various cyberthreats.
Do You Need to Be Both NIST 800-171 and CMMC 2.0 Certified?
Since the release of the CMMC framework in January 2020, contractors have been asking if they need to comply with both NIST 800-171 and CMMC. The answer is yes. NIST 800-171 is not enough to address the growing number of cyberthreats against DoD contractors, which is why the CMMC framework was created. However, contractors need to implement various NIST controls before they can be CMMC certified. As previously mentioned, CMMC compliance is now required for contractors to bid and win DoD contracts.
If your company is not yet CMMC certified, a managed IT services provider like Charles IT will help you achieve certification. We'll perform a gap assessment to identify potential danger spots and areas of weakness in your company's cybersecurity processes. Our IT experts will then provide you with a remediation plan to ensure you pass your CMMC audit. Fill in the gaps in your business’s cybersecurity, starting with a gap assessment.
Editor's Note: This blog was originally published on August 21, 2020. It was edited for accuracy on July 30, 2023.

.png)



