
If you’ve been reading about how to increase security in your business, you’ve most likely stumbled across multi-factor authentication.
Multi-factor authentication will mean something different based on the industry you operate in. For example, a construction company will utilize different factors compared to a fully remote software company.
Understanding the characteristics of different types of authentication factors will help you decide which ones are right for your business.
How Does Multi-Factor Authentication Work?
At the most basic level, multi-factor authentication adds another layer of security to your system. Instead of just having users log in using a password, they will be required to enter additional information that is difficult to guess by hackers.
There are three main authentication factors that you can implement, which are something the user knows, something the user has, and a physical quality of the user, like a fingerprint.
.png?width=568&height=379&name=MFA%203%20Main%20Factors%20-%20Charles%20IT%20Blog%20Graphic%20(5).png)
For example, if you are using an ATM in your everyday life, you have your physical bank card, plus your PIN number to access your account. This is an example of something you have, and something you know. Applying this theory to your business is not only cybersecurity best practices, but can also save you money on your cyber insurance policy, as most providers now require policy holders to have MFA implemented.
Depending on the complexity of your system and the information you are trying to protect, one of these options might be more advantageous over the other.
Keep in mind that the factors most useful for your company are based on your workforce. If you have a remote workforce, swiping a physical card wouldn’t be very effective. However, if you are in an office, this could be a factor to consider.
What are the Different Types of Multi-factor Authentication?
There are dozens of multi-factor authentication factors that your business can implement. Nevertheless, here are a few common and generally cost-effective ones to consider:
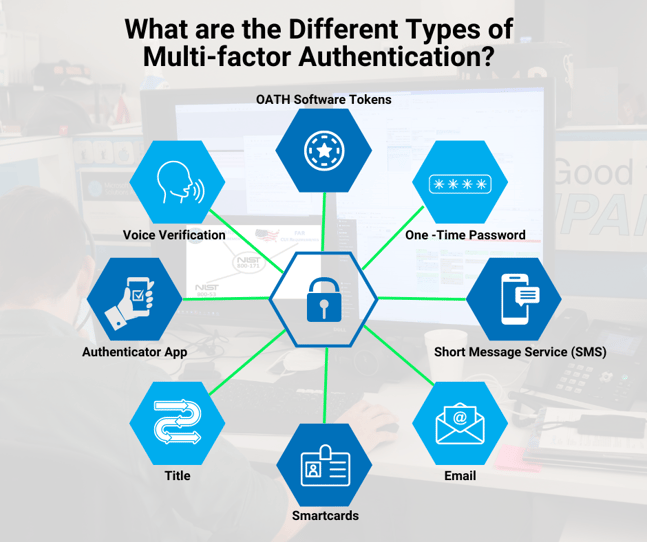
- One-Time Password (OTP) – This is a temporary verification code that is only active for a short duration. After the time expires, a new code will need to be submitted.
- Short Message Service (SMS) – This authentication avenue sends a short text or code to the user’s phone without requiring a subscription or outside application.
- Email – An email authentication will send a unique link for the user to sign in to.
- Smartcards – This type of multi-factor authentication gives the users a physical card to swipe for access.
- Title – This is a software program that is integrated into mobile apps and functions on cryptographic methods. It is commonly used to authenticate a device and reduces the need to switch between different platforms.
- Authenticator Apps – Authenticator apps are becoming more popular as users rely on their smart devices. The user’s phone number is linked to their account, and they will be sent a unique code to enter for access.
- Voice Verification – This is an inherent factor as the system will recognize the tone of the voice. Many advanced voice verification systems also scan the movement of the mouth during speech.
- OATH Software Tokens – This verification avenue uses open-source authentication on the RFC 4226 HOTP algorithm. Tokens can be configured to your specific business’s needs, such as time or event-based.
Most of these factors can be tailored to your business. For example, instead of a short message service, you could have a program that calls users with a code. Tailoring the factors to your organization will help ease the transition and promote the use of the added security features.
Choosing Between Factors
Selecting the right types of multi-factor authentication is important for the security and compliance of your organization. You want to choose authentication features that users in your organization will actually implement without compromising the existing security measures already in place.
If you are unsure of which factors seem reasonable and cost-effective for your organization, reach out to the team at Charles IT. We can work alongside you to uncover the factors that benefit your organization the most. Reach out today to learn more!

.png)


