Organizations face a variety of risks; one of the most critical being cybersecurity risks, which can affect day-to-day operations, threaten compliance, and tarnish your company’s reputation.
To help minimize your overall organizational risks, the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) can be of great use. It guides organizations in identifying, assessing, and mitigating cybersecurity-related risks. The second benefit of using the NIST framework is that it provides a common language for professionals to discuss and share information about their cybersecurity practices, identify and prioritize actions, and measure progress.
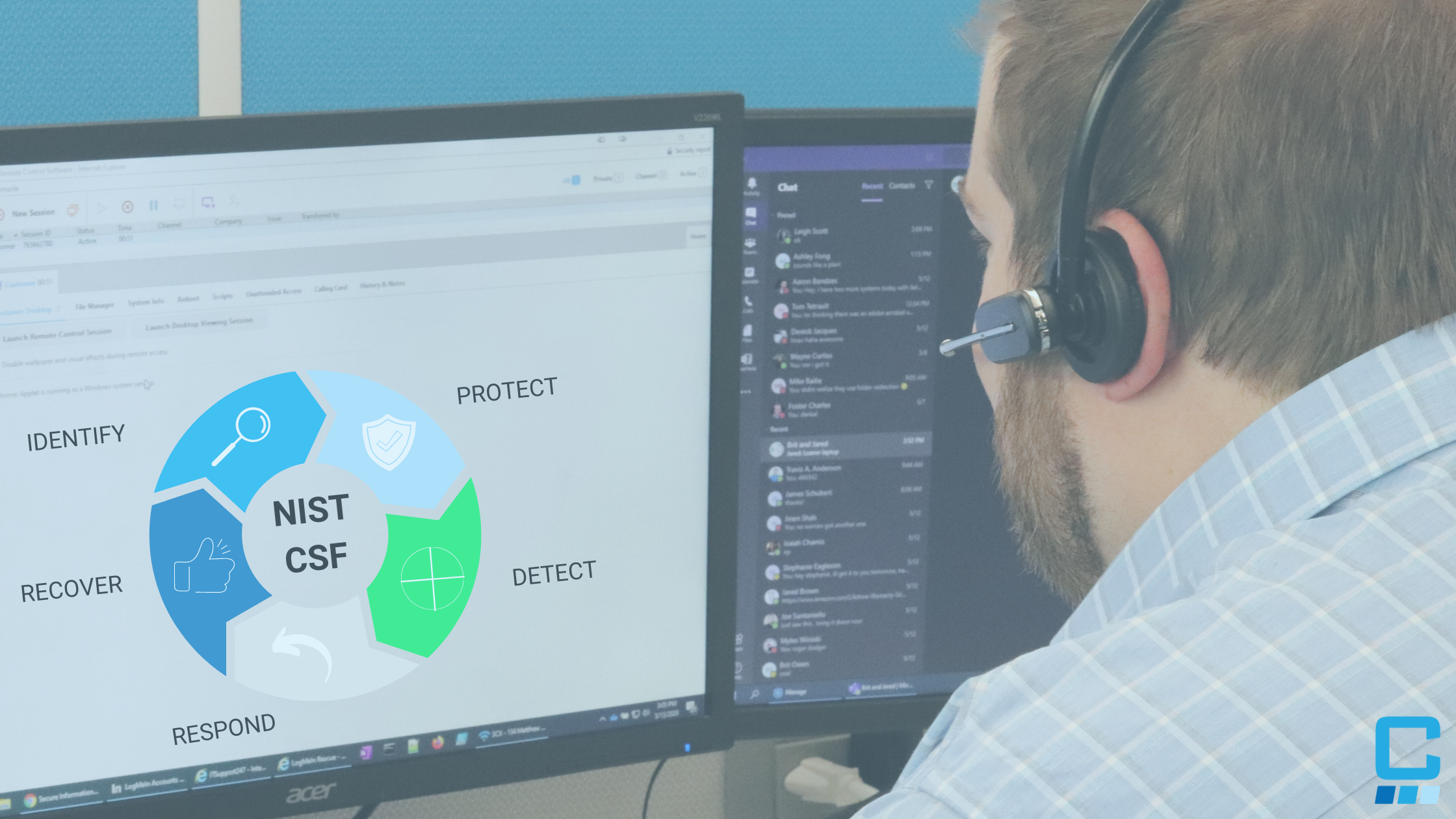
Specifically, NIST CSF can help you assess your cybersecurity risks by providing guidelines in five core areas, which are outlined in our previous blog post, Getting Started with NIST Cybersecurity Framework.
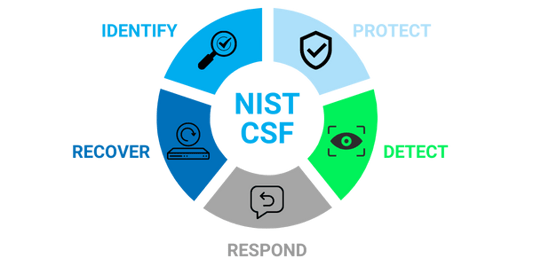
Now, let’s take a closer look at how each of these core areas help to assess your organizational risk.
Assess Your Risk
Identify your business’ environment
The NIST framework recommends properly identifying your business’ systems, people, assets, data, and capabilities when assessing risk. In other words, you need to know how data flows through your organization and who has access to it, so that it becomes easier to determine where vulnerabilities may exist and what data needs to be protected.
As an example, knowing which systems are most important to your company’s core operations can help you prioritize your cybersecurity efforts and better understand the potential impact of a breach. It can also help you manage permissions to confidential systems and data, preventing unauthorized access that could lead to a breach.
Safeguard, Restrict, & Train
Protect Your Data
As is expected from a cybersecurity framework, it provides guidance on identity management, authentication, and access controls to help organizations safeguard data and systems. This includes verification of user identity and devices to ensure that a user is who they claim to be, thus reducing the risk of data breaches and unauthorized access to critical systems.
The framework also provides data security solutions to help you protect your data from unauthorized access or disclosure. These solutions include encrypting data in transit and at rest, as well as managing access to data. To maintain systems and keep them updated and secure, there is additional guidance provided. This comprises topics on patching systems, updating software, and monitoring for vulnerabilities.
Finally, NIST standards will guide your business in implementing cybersecurity awareness training to help employees understand cybersecurity risk and their role in protecting organizational assets. By training employees on how to identify potential threats, report incidents, and follow security procedures, you can reduce the likelihood, and minimize the impacts, of successful attacks.
|
Related reading: Security Solutions That Will Keep You from Getting Fined |
Establish Your Baseline
Detect Cyber Anomalies
Being able to quickly identify anomalous activity is critical in minimizing organizational risks. This requires businesses to have visibility into all systems, including monitoring capabilities and incident response procedures. NIST CSF helps you accomplish this by providing guidance on cybersecurity event detection, such as how to implement intrusion and malware detection tools.
Organizations can also use the framework to establish baselines for what is considered normal activity within their system. This allows for easier identification when something is out of the ordinary, which could indicate a security incident. Having bases for calculation or comparison enables your business to increase your situational awareness and reduce the time it takes to detect and respond to incidents.
Address, Contain, & Improve
Respond to Cybersecurity Incidents
NIST CSF provides guidance on how to develop and implement appropriate processes to address a cybersecurity event once it’s been detected. This includes steps to contain the event, eradicate the threat, recover your data, and restart your business operations. Having a well-defined incident response plan in place allows you to quickly and efficiently address a security incident.
The cyber security framework also recommends conducting post-incident reviews to identify lessons learned and areas for improvement. This helps to ensure that your organization is constantly improving its cybersecurity posture and is best prepared to respond to future incidents, which reduces any compliance or reputational risks.
Backup, Maintain, & Minimize Impact
Recover Your Data
Having a business recovery strategy in place minimizes the impact of cybersecurity events. The NIST standards provide guidance on backing up data, maintaining system availability, and reconstructing systems and data. This includes steps on how to test your backup systems regularly to ensure that they are working properly and you can recover data in the event of a cybersecurity breach.
Additionally, it recommends establishing a business continuity plan to help your organization remain operational in the event of a major cybersecurity incident. A guide is provided on how to identify critical functions, develop alternate plans for providing these functions, and train employees on the established continuity plan. By having a well-defined recovery plan, you can minimize the impact of a security incident and get your business back up and running as quickly as possible.
NIST CSF is a great resource for businesses looking to minimize organizational risks by strengthening their cybersecurity posture. If you're not sure where to begin, our team of experts at Charles IT can help you get started on your cybersecurity journey. Contact us today to learn more!

.png)


