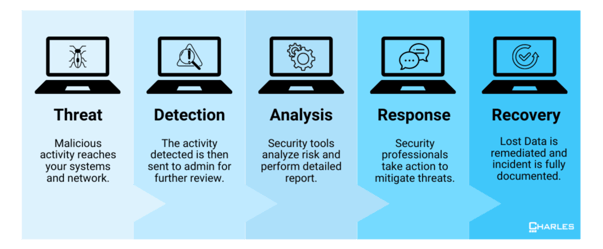
Navigating the ever-changing world of cybersecurity can be overwhelming, particularly for businesses that lack the resources or expertise to maintain a strong in-house security posture. That's where Managed Detection and Response (MDR) services come in – they act as your standby team of guards. However, with numerous providers offering different levels of protection, choosing the right MDR partner can seem like a daunting task. To help you make an informed decision, we have compiled five essential questions to ask your potential MDR provider:
businesses that lack the resources or expertise to maintain a strong in-house security posture. That's where Managed Detection and Response (MDR) services come in – they act as your standby team of guards. However, with numerous providers offering different levels of protection, choosing the right MDR partner can seem like a daunting task. To help you make an informed decision, we have compiled five essential questions to ask your potential MDR provider:
1. Unmasking the Shadows: How Do You Identify and Prioritize Security Gaps in My Environment?
To truly understand the vulnerabilities within your network, it's like illuminating hidden weaknesses that are lurking in the shadows. A highly skilled MDR provider should utilize a comprehensive approach to reveal these security gaps, which includes:
- Vulnerability Scanning: Automated tools thoroughly scan your systems and applications to detect any known weaknesses, ensuring that even the most elusive vulnerabilities are identified.
- Risk Assessment: Your provider thoroughly examines your industry, company size, and attack surface, constructing a comprehensive map of potential threats and vulnerabilities that are tailored to your specific environment.
- Threat Intelligence: By leveraging extensive databases of emerging threats and attack vectors, your MDR provider proactively stays ahead of the curve, predicting and mitigating evolving threats before they have a chance to exploit any vulnerabilities.
- Penetration Testing: Ethical hacking simulations replicate real-world attacks, revealing vulnerabilities that automated tools may overlook. This process offers invaluable insights for taking proactive measures in defense.
- Continuous Monitoring: Real-time monitoring is conducted on logs, events, and network traffic to detect any suspicious activity, providing immediate insights into potential threats before they have a chance to escalate.
- Security Configuration Audits: Your provider carefully examines your systems and applications, making sure that their configuration aligns with industry best practices, thereby reducing potential attack vectors.
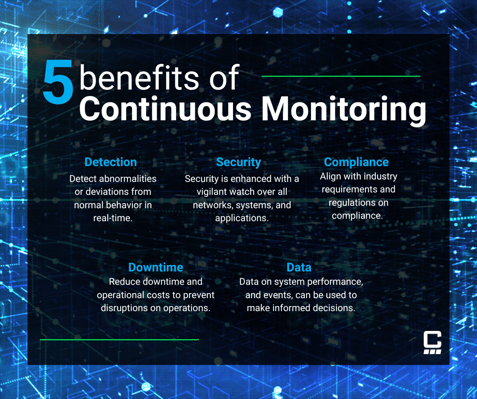
It's important to note that identifying vulnerabilities is just the initial phase. After identifying these gaps, it's crucial for your internal or external IT team to prioritize them based on their potential impact and exploitability. They will carefully consider factors such as the ease of exploitation, the potential damage that an attacker could cause, the likelihood of an attack occurring, the effort required for remediation, and any compliance requirements. This evaluation ensures that the most critical threats are addressed first.
2. Synergy in Action: How Do You Leverage and Integrate with My Existing Security Technologies?
Disrupting your existing security ecosystem can have serious consequences. An effective MDR provider should seamlessly integrate with your established security tools, maximizing their effectiveness and avoiding any potential issues. Look for providers with a proven track record of integrating with popular security solutions, offering pre-built connectors, and customizing their integration approach to meet your specific needs. It's crucial to prioritize seamless data privacy and compliance, so make sure your provider adheres to relevant regulations and security standards.
3. Unveiling the Essentials: What are the Basic Capabilities I Should Expect When Shopping for MDR Services?
No company should have to accept a basic approach to security. A comprehensive MDR service should include:
- 24/7 Security Monitoring and Threat Detection: Your provider maintains constant vigilance, scanning for threats and suspicious activity to ensure the protection of your network, even during your downtime.
- Incident Response and Containment: When a security incident arises, your MDR team promptly springs into action, swiftly containing the threat and minimizing any potential damage. This proactive approach prevents minor issues from escalating into major crises.
- Forensic Analysis and Root Cause Investigation: Understanding the source and nature of an incident is vital in order to prevent similar incidents in the future. Your provider should conduct a thorough analysis of the incident, identifying the root cause and implementing necessary measures to address it.
- Threat Intelligence and Vulnerability Management: Staying ahead of the game is crucial. Your MDR provider should provide you with ongoing updates on emerging threats and take proactive measures to address vulnerabilities before they can be exploited by attackers.
- Security Awareness Training and Phishing Simulations: Educating your employees is crucial for proactive defense. It's imperative that your provider offers comprehensive training programs and simulations to empower your team with the necessary knowledge to effectively identify and avoid phishing attacks and other social engineering tactics.
- Reporting and Compliance Management: Staying informed is crucial. Your provider should provide you with detailed reports on the threats detected, incidents resolved, and vulnerabilities mitigated, all while ensuring compliance with relevant regulations.
4. Measuring the Impact: How Do You Evaluate the Effectiveness of Your MDR Services?
Transparency is crucial. Instead of solely relying on your provider's claims, you can request metrics that provide evidence of their service's effectiveness. Seek out providers who measure performance through metrics such as:
- Time to Detection: How quickly are threats identified and contained?
- Mean Time to Resolution (MTTR): How swiftly are incidents resolved?
- Number of Threats Detected and Blocked: Concrete evidence of their proactive threat hunting.
- Vulnerability Mitigation Rate: A clear indicator of their effectiveness in patching security gaps.
Regular reports should be provided to keep you informed of the progress and effectiveness of your investment in MDR. Additionally, service-level agreements (SLAs) should offer specific performance outcomes, providing you with peace of mind and accountability. Feel free to request references from other customers to gain firsthand insights into the quality of service provided.
5. Trust and Expertise: How Do You Ensure the Qualifications and Expertise of Your Security Analysts?
Your MDR provider is only as good as its people. The professionals responsible for safeguarding your critical data should undergo thorough training. Here are the key factors to consider:
- Certifications and Experience: Look for providers whose analysts possess industry-recognized certifications such as CISSP, CISA, and SANS GPEN. It's also important to consider their extensive experience in security operations and incident response.
- Ongoing Training and Development: Leading providers prioritize the ongoing development of their analysts, investing significantly in their continuous learning. Look for programs that ensure analysts stay up to date with the latest threats, attack vectors, and best practices in security.
- Threat Hunting Prowess: It's crucial to have a team of analysts who are skilled and equipped to proactively hunt for threats and uncover any hidden risks in your environment, ensuring that attacks are stopped before they can cause any damage.
- Communication and Collaboration: Clear and effective communication plays a crucial role in establishing trust and ensuring a seamless incident response. It's important to select a provider whose analysts possess the ability to articulate complex technical issues in a straightforward manner and collaborate efficiently with your internal or external IT team.
- Cultural Fit: Seek out a provider that shares your company's values and aligns with your approach. A harmonious partnership promotes trust and collaboration, which ultimately leads to improved outcomes.
Selecting the appropriate MDR provider is a crucial choice. By posing the appropriate questions and thoughtfully assessing these supplementary factors, you can confidently choose a partner who will safeguard your organization against ever-changing cyber threats. This will enable you to concentrate on what truly matters – your business.
Keep in mind that the ideal MDR provider is more than just a vendor; they should be a collaborative partner. Look for a provider that prioritizes transparency, aligns with your security goals, and equips your team with the necessary knowledge and tools to effectively navigate the constantly evolving threat landscape.
If you need assistance on your search for a reliable MDR partner, Charles IT is here to help! Whether you need guidelines on what to look for or security integration with your MDR provider, book a call with us today to kickstart your path to ideal cyber hygiene.