
With cyber attacks increasing at a rapid rate, the importance of securing your organization at every level is crucial. What's one of the best ways to secure your network? You guessed it - Multi-Factor Authentication (MFA)!
From Q4 of 2021 to Q1 of 2022, there was a 14% increase in data breaches and compromises in businesses. That's the third straight year of attacks increasing in Q1. It's important to ask, why is multi-factor authentication important in this scenario?
MFA is a critical piece of security when covering all of your cybersecurity bases. Passwords are no longer enough to keep your company's email systems, bank accounts, databases, and other online accounts secure. You need to further boost your IT security and your account login process by enabling a MFA system.
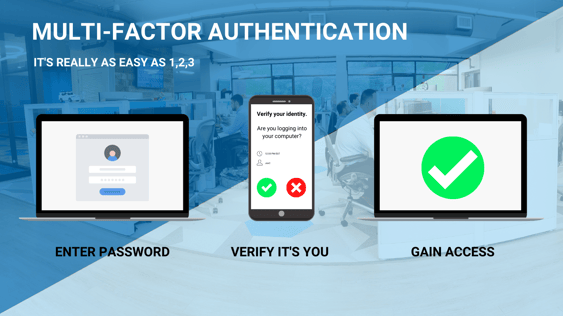
So, what does multi-factor authentication mean? MFA consists of an additional piece of information to log in to company systems. This can be something you know, something you are, or something you have. For example, if you sign in with your password (something you know) you then get a push notification to your personal device that you must approve (something you have).

Lets dig into the importance of multi-factor authentication and why you should be using it.
Why Use Multi-Factor Authentication?
Aside from reducing the risks of poor password practices, there are many other reasons why businesses must enable MFA.
Cybercriminals Target Passwords
Verizon’s 2022 Data Breach Investigations Report found that credentials are the most sought-after data type because cybercriminals can use these to masquerade as legitimate users on a system. In fact, according to another report by IBM, the use of stolen or compromised credentials is the top cause of data breaches. To make matters worse, over 15 billion stolen credentials collected from more than 100,000 breaches are on the dark web, primed for the taking.
Cybercriminals steal passwords by employing various tactics, such as:
- Phishing – tricking users into providing sensitive information
- Keylogging – secretly recording keystrokes of users
- Pharming – installing a malicious code onto a computer, which misdirects users to a fraudulent site in a bid to steal their personal data
Unfortunately, these tactics aren't just used to trick individuals - but also huge corporations that collect, store, and manage their customers’ data.
MFA Minimizes the Risk of Security Breaches
With MFA enabled, a cybercriminal that successfully obtains a user's credentials would still need to provide the second factor to complete the login process and access the account.
This extra layer of security effectively blocks most attacks stemming from compromised accounts. That's why Google automatically enabled 2FA for their 150 million users in 2021, which resulted in a 50% decline in compromised accounts. Moreover, in the same year, MFA was mandated for all federal agencies in the United States.
Compliance Regulations
The regulatory market has a growing focus on personally identifiable information.
Most compliances either require some version of MFA, or are reforming their framework to include requiring MFA in order for companies to be considered compliant. Frameworks like PCI for payment processing, HIPAA for healthcare companies, and GDPR for companies operating in the EU. With industries that are heavily compliant, there is typically sensitive data that those compliance frameworks are trying to protect.
Many of these organizations have "over the top" MFA implemented - where multiple factors are required to access the network, but not the systems and apps. The systems and apps are where most organizations' critical data is stored, which is why it's important to implement MFA to all layers of your infrastructure.
layers of your infrastructure.
Zero Trust Security
Multi-factor authentication is an essential piece to a zero trust security model. The zero trust model is quickly being adopted by companies and compliance frameworks because of it's end-to-end security. It boils down to no one being trusted by default - inside, or outside of your network. What does this mean exactly? No one - not even C-level employees - has direct access to any resources on your company network.
This is where MFA comes in, it makes it simple to sign in and confirm it's you accessing the network. This helps a zero trust model become surprisingly easy to implement and maintain, as a third-party MFA host can handle all of your push notifications confirming employees identities.
Secure Against Brute Force
Last year, according to the Verizon 2022 Data Breach Investigations Report, 45% of data breaches involved hacking, and 80% of those breaches involved brute force or use of lost or stolen credentials. This means that hackers were either guessing passwords correctly, or receiving them "voluntarily" through a social engineering attack, like phishing. Having a MFA solution in place makes it so a hacker cannot access the network with just a guessed or stolen password, as the authentication for sign in will go to the employee whose password was compromised.
With security awareness training, said employee would know to not approve a MFA push without having signed in themselves!
In Summary
These are a few of the overarching reasons why MFA should be implemented in all organizations as a cybersecurity best practice. If your organization deals with sensitive data, it is borderline essential for you to have some sort of MFA solution in place. What's more, even with MFA in place in your organization, it's important to match that with security awareness training for your employees. That way, your organization won't run into an attack like the Uber breach from September of 2022.
Ready to get started with MFA? Let the IT experts of Charles IT enable MFA for you to ensure its smooth implementation. Get in touch with us today!




