.png)
Any Department of Defense (DoD) contractor must comply with the security standards of the Defense Federal Acquisition Regulation Supplement (DFARS) before it can be given access to controlled unclassified information (CUI).
If your organization is not DFARS-compliant, you risk losing your DoD contracts and chances of bidding on contracts in the future -- don't worry, we got you! Let's talk about the 14 security control families you must comply with to meet DFARS standards.
What Is DFARS Clause 252.204-7012?
 The DFARS is a set of cybersecurity standards imposed by the DoD on external suppliers and contractors to safeguard the confidentiality of CUI based on the cybersecurity standards laid out in the National Institute of Standards and Technology Special Publication 800-1771 (NIST 800-171). The DFARS clause 252.204-7012 revolves around meeting the requirements of 14 control families to ensure the safeguarding of covered defense information and timely reporting of cyber incidents.
The DFARS is a set of cybersecurity standards imposed by the DoD on external suppliers and contractors to safeguard the confidentiality of CUI based on the cybersecurity standards laid out in the National Institute of Standards and Technology Special Publication 800-1771 (NIST 800-171). The DFARS clause 252.204-7012 revolves around meeting the requirements of 14 control families to ensure the safeguarding of covered defense information and timely reporting of cyber incidents.
|
Related article: A Guide to Understanding DFARS Requirements |
No. 1 | Access control
Access control focuses on the process of allowing or denying a user's request to enter company facilities, use CUI, and make use of information processing services. System-based access controls, also known as logical access controls, determine who should be given access to system resources and the type of access permissions.
For instance, users should only be given access to the information and resources they need to perform their tasks, and access to non-job-related information should be prohibited. In addition, the type of access permission, such as read and execute, read-only, write, and full control, should also be limited to ensure unauthorized access to CUI.
No. 2 | Awareness and Training
Employees are considered one of the weakest links in a company's cybersecurity defense. Oftentimes, workers are unaware of how their actions impact the security of the company infrastructure. For example, a user who can't identify a phishing email may end up clicking on a compromised link that installs malware or takes that user to a fake site designed to steal sensitive information. Raising cybersecurity awareness and providing regular training will help employees understand their security responsibilities and instill best practices in identifying various cyber threats
|
Related article: 5 Tips to Achieve DFARS Compliance |
No. 3 | Audit and Accountability
DoD contractors are required to create, retain, and protect system audit records to monitor, analyze, investigate, and report all unauthorized, unlawful, and inappropriate activities associated with CUI. These records can help trace specific user actions to find whoever carried out the unsanctioned activities and hold them accountable if CUI is leaked or compromised.
No. 4 | Configuration Management
Configuration management is a group of activities designed to maintain the integrity of information technology systems and products by controlling the configuration process. It involves identifying and documenting the correct system settings, performing a security impact analysis, and managing all changes using a change control board.
Without proper documentation, you wouldn't know if changes made to one system would have an adverse effect on another business-critical system. This lack of insight can prevent your employees from performing their tasks, or worse, leave your infrastructure open to cyberattacks that could compromise CUI.
No. 5 | Identification and Authentication
This control family identifies users requesting access to CUI and authenticates their identity before being granted access to CUI and other system resources. It is a vital part of cybersecurity because it acts as a first line of defense that prevents unauthorized people from accessing your system.
Apart from securing the initial login process, an effective identification and authentication system is also able to track whether an authenticated user is still active within the system. For instance, a user who is no longer using a terminal or has been inactive for some time is automatically logged off. This prevents unauthorized people from using that same terminal that might have access to CUI.
No. 6 | Incident Response
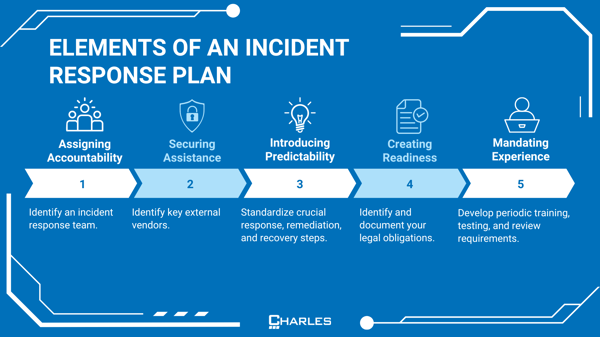
An incident response plan allows your organization to react to emergency events such as natural disasters, cyberattacks, and utility outages. Critical to an incident response plan is a solid backup and recovery strategy, which allows you to restore data from a recent version if necessary. For example, an important file that was accidentally deleted by a user or corrupted because of a malware attack can be restored from a backup.
Without an incident response plan, emergency events can quickly spread, leading to escalated damage and serious harm to your company. An effective incident response strategy should contain sufficient preparation, detection, analysis, containment, recovery, and user response activities. These incidents should be tracked, documented, and reported to management and/or internal and external authorities.
No. 7 | Maintenance
Implement system maintenance procedures that will ensure your infrastructure is working properly and prevent software and hardware failures. There are various ways to do this. Controlled maintenance refers to scheduled maintenance conducted based on a manufacturer's specifications. Corrective maintenance, on the other hand, is performed when a system or part of a system fails. Improper system maintenance or failure to conduct one can lead to the unauthorized disclosure of CUI, which can compromise its privacy and confidentiality.
No. 8 | Media Protection
This control family focuses on the protection of system media, both digital and non-digital. Examples of digital media include external or removable hard drives, compact discs, magnet tapes, and flash drives. Examples of non-digital media include microfilm and paper.
There are several ways to ensure media protection. First, access to CUI or other resources contained in system media should be limited to authorized personnel only. Employees should also be able to use only digital media approved by an asset manager to store CUI. Policies should be implemented on how to remove CUI from media so that the information cannot be reconstructed or retrieved once the media is released for reuse or destroyed. Media protection also includes limiting the use of personal mobile devices capable of storing information inside restricted areas.
No. 9 | Personnel Security
Since DoD contractors work with proprietary and sensitive information, accidental or intentional disclosure of that information can result in financial and reputational damage. This is why contractors should be extra careful when hiring new workers and reassigning or terminating employees. An extensive background check and screening process must be conducted before hiring new employees to ensure they pass established security criteria and are trustworthy.
Employees who are transferred or reassigned should be given a new set of system and physical access permissions, while their old ones are returned or disposed of properly. Terminated employees must have their access disabled, and the employers should also retrieve all system-related property and information used by the terminated employees.
Personnel security aims to reduce the risk that employees pose to CUI and other company assets through the exploitation or malicious use of their access to organizational resources.
No. 10 | Physical protection
Physical protection refers to the measures taken to protect buildings, systems, and supporting infrastructure from threats related to their physical environment. Sensitive areas in your facility should implement safeguards such as security guards, closed-circuit television cameras, locks, and card readers so that only authorized personnel can access these areas, ensuring CUI security and safety.
In addition, contractors must ensure their facility is safe from natural disasters, man-made threats, and damaging nearby activities such as civil disorder, and electromagnetic interference to prevent or minimize disruptions to your operations.
No. 11 | Risk Assessment
Risk assessments can identify and prioritize risks to your company's assets, operations, employees, and partners. It will help you create effective remediation strategies to address various security-related issues such as supply chain attacks and advanced persistent threats. For example, it can help you defend your systems from vulnerabilities brought about by the implementation of new technologies.
No. 12 | Security Assessment
A security assessment tests and/or reviews your company's operational, management, and technical security requirements. These tests ensure that business components have been implemented correctly, are operating properly, and are producing the desired results based on your infrastructure’s security requirements. Just like in a risk assessment, you must create a plan of action to address deficiencies and minimize or eliminate any vulnerabilities in your current security policies.
No. 13 | Systems and Communications Protection
This control family focuses on the confidentiality of CUI at rest and in transit. System and communications protection creates barriers that limit access to publicly accessible information within your system. It also lets you monitor and control communications at internal and external boundaries to prevent unauthorized transfer of CUI. Additionally, CUI must be encrypted before transit to prevent unauthorized modification and disclosure.
No. 14 | System and Information Integrity
System and information integrity ensures that the CUI being accessed has not been tampered with or damaged by a system error. It requires contractors to identify, report, and correct system flaws in a timely manner. Contractors must also take the appropriate measures to protect their infrastructure from malicious codes that can compromise the integrity of CUI. This includes installing antivirus software, updating software and applications, and monitoring and addressing security alerts.
Charles IT helps with complying with DFARS standards is proof that you have the security measures in place to keep CUI safe. If you want to know more about DFARS compliance, contact us!
Editor's Note: This post was originally published in May 2021 and has been updated for accuracy and comprehensiveness.

.png)



