.png)
Most data breaches are easily avoidable if you take a proactive approach to manage your IT environment. Unfortunately, many businesses have historically relied only on reactive measures, such as conventional antivirus software. While these measures are still important today, they only kick in once a threat has already made it past your network, potentially causing serious disruptions to your company.
More than ever, businesses must focus on proactively identifying and closing vulnerabilities in increasingly complex and disparate IT environments. This is essential for achieving a high level of cybersecurity maturity, as well as achieving respective compliance frameworks.
What is an External Vulnerability Scan?
 An external vulnerability scan is one such proactive measure that thoroughly scans your digital assets from an outside perspective. You can think of it as proactive IT security monitoring. In many ways, a vulnerability analysis works like an actual cyberattack in that it uses similar methods to those hackers use to penetrate your network.
An external vulnerability scan is one such proactive measure that thoroughly scans your digital assets from an outside perspective. You can think of it as proactive IT security monitoring. In many ways, a vulnerability analysis works like an actual cyberattack in that it uses similar methods to those hackers use to penetrate your network.
System vulnerability scanning is essential for achieving and maintaining compliance by proactively identifying vulnerabilities on a regular basis. It's highly recommended that companies carry out external vulnerability scans on a quarterly basis and run an additional vulnerability scan every time a significant change is applied to the company's infrastructure.
External vulnerability scanning evaluates your entire network for potential issues that could leave your digital assets exposed to the outside world. As such, it is also known as perimeter scanning. This includes scanning every user account and all endpoints, such as vulnerable web applications and network-layer vulnerabilities. It also incorporates scanning of remote work environments, such as cloud-hosted virtual machines and user accounts. After all, the concept of 'the perimeter' has changed a lot in the age of mobile computing, hybrid and remote work, and internet-connected smart devices.
| Related Article: How External Vulnerability Scanning Can Help with SOC 2 Data Security |
Issues That External Vulnerability Scanning Can Reveal
1. Identify Unpatched Vulnerabilities
Most vulnerabilities are easy enough to remediate, but you need to know where they are in order to fix them. Many issues, such as unused accounts and outdated operating systems and firmware, are frequently overlooked. With more endpoints than ever before, hosted across an increasingly wide range of different systems, automation is an essential part of business processes today and can make identifying vulnerabilities that much more challenging.
A network security scanner can help to achieve complete visibility into your network assets. This way, you can identify operating systems and devices with outdated security protocols or in need of critical security updates that haven't been patched and address the issues right away.
2. Locate Poorly Secured Endpoints
There are many possible single points of failure in today’s typical computing infrastructures. One of
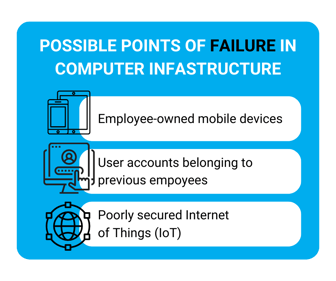
the biggest challenges is locating them. Some of the most common cases include employee-owned mobile devices, user accounts belonging to previous employees, or poorly secured internet of things (IoT) devices.
Network security scans build a complete inventory of every networked device and system, including those hosted in the cloud. It will then scan these systems for any potential issues, such as weak access controls and problematic firmware.
3. Resolve Network Configuration Errors
While cloud companies are often the first to get the blame when it comes to data breaches, the truth is that most bad actors target poor configurations. The responsibility to maintain these configurations often falls to the end user. This includes things like enforcing password policies, multi-factor authentication (MFA or 2FA), and other user-level access controls. In other cases, it might be a matter of changing security protocols and applying end-to-end and endpoint encryption.
Vulnerability scanning provides a complete view of your current configurations and highlights any potential risk areas, such as weak user access credentials and other issues, giving you a chance to resolve them before it’s too late.
4. Prepare for Network Topology Changes
Today’s business networks are dynamic and ever-changing. New user accounts and systems are added all the time, along with new services and resources being rolled out to meet rising demands. While unavoidable, network topology changes and updates increase risk levels if they aren't applied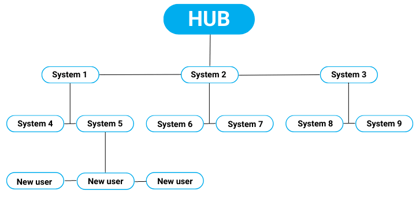 according to rigid compliance standards.
according to rigid compliance standards.
Since it’s risky to carry out changes and upgrades without knowing where your existing vulnerabilities lie, vulnerability scanning gives you the necessary insight to prepare for changes and upgrades without adding unnecessary risk.
Charles IT provides comprehensive vulnerability scanning to identify potential risk areas and help you refine the security of your network. Call now to schedule your assessment!
Editor's Note: This post was originally published in February 2021 and has been updated for accuracy and comprehensiveness.

.png)




