It's Cybersecurity Awareness Month once again, a time to reflect on the current state of cybersecurity and what you can do to safeguard your business. Below are five key takeaways from 2022 that can help bolster your company’s cybersecurity posture.
1. Remote working is becoming a large part of the workforce, and it requires extra cybersecurity measures with emphasis on certain solutions.
 Charles IT's ideal remote work set up.
Charles IT's ideal remote work set up.
As businesses continue to settle into a hybrid or fully remote work setup, cybersecurity should take precedence. After all, with employees using potentially unsecured home networks and personal
devices for work, there are more entry points for cybercriminals to exploit.Securing your corporate network is crucial, but remote workers now need additional tools and resources to stay safe. This includes investing in cybersecurity solutions like virtual private networks (VPNs), remote access software, and endpoint management tools, as well as training employees on how to use these tools properly.
Creating a remote or hybrid work policy that outlines the expectations and procedures for employees is also a must. This policy should address everything from working hours and break times, to the type of devices and software allowed for work. By having a clear and concise policy in place, you can keep the entire team on the same page when it comes to cybersecurity.
2. Continuous cybersecurity education and training are crucial for both businesses and individuals.
Given that data breaches, social engineering scams, and other security threats are constantly evolving, it's only prudent to keep up with the latest trends and best practices. This means investing in the company’s continuous cybersecurity education and training.
There are a number of ways to do this, such as attending webinars and conferences, reading industry-specific news and blogs, and taking online courses. You can also find plenty of resources on the Cybersecurity and Infrastructure Security Agency and the National Cybersecurity Alliance websites.
Partnering with a reliable managed IT services provider (MSP) is perhaps the best way to stay on top of relevant cybersecurity insights. An MSP’s team of experts can also ensure that you and your employees have the knowledge and skills needed to thwart and mitigate the latest threats.
3. Cyber incident response plans need to be tested and updated regularly.
 Charles IT Dev Nights are a time for the team to get together and try out new products or services, then discuss whether or not they will be useful for our company.
Charles IT Dev Nights are a time for the team to get together and try out new products or services, then discuss whether or not they will be useful for our company.
No matter how strong your company's cyber defenses are, you may still suffer a severe security breach. That's why you must develop incident response plans for various types of scenarios, like cybercrime, data loss, and service outages.
Make sure to review and update your response plans regularly. This ensures that they're relevant and useful in the event of a cybersecurity incident. You should also test your plans periodically to see how well they work in practice. This can be done through tabletop exercises, which involve key stakeholders going through each step of a response plan to see where improvements can be made.
4. Strong passwords and MFA are essential for good cybersecurity hygiene.
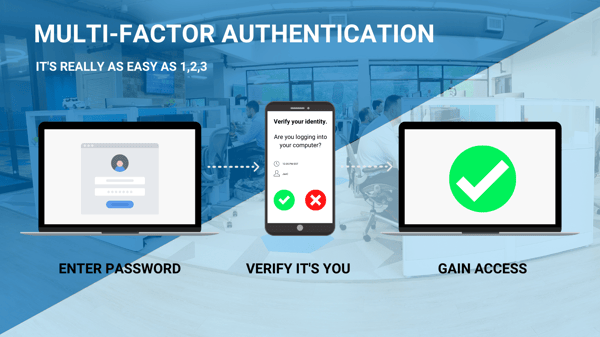
Always use strong and unique passwords. These usually contain a mix of letters, numbers, and symbols, with uncommon words and phrases. You can use a password manager to generate strong passwords for you, and keep them all in one secure vault for easy retrieval.
Moreover, enabling multi-factor authentication (MFA) for all of your online accounts is strongly recommended. MFA adds an extra layer of security by requiring users to confirm their identity with other factors, like a code generated by an app, a face scan, or fingerprint scan.
5. Applying software patches and updates in a timely manner is crucial to mitigating cybersecurity risks.
Most, if not all, software programs have security vulnerabilities that can be exploited by cybercriminals. Therefore, it’s crucial to your business’s safety to always have the most recent patches and updates. But this can be a challenge if you have a lot of devices and programs to keep track of.
Fortunately, a good MSP will have a system in place for monitoring and applying updates in a timely manner. This not only takes the burden off of you and your team, but it also ensures that all of your devices and programs are secured against the latest known threats.
While Cybersecurity Awareness Month is a perfect time for businesses to review and improve their cybersecurity posture, it's important to remember that cybersecurity is a year-round effort. By staying up to date on the latest threats, implementing strong security measures, and continuously educating yourself and your employees about good cybersecurity practices, you can keep your business safe from harm.
Don't know where to start? Our team of cybersecurity experts at Charles IT can help you assess your risks and develop a comprehensive cybersecurity strategy tailored to your business. Drop us a line today!
Editors note: This blog was originally written in 2022 and updated in 2024 for accuracy.
FAQs
Businesses should review and update their incident response plans regularly to ensure they stay relevant and effective. This includes periodic testing, such as through tabletop exercises, to identify any gaps and make necessary improvements to your IT security plan.

.png)




