
The Cybersecurity Maturity Model Certification (CMMC) is a set of guidelines for implementing cybersecurity measures across Department of Defense (DoD) contractors. CMMC was designed as a supplement to DFARS 7012, which the DoD uses to regulate Controlled Unclassified Information (CUI). To ensure that the many contractors and subcontractors operating in the defense industrial base (DIB) supply chain are safeguarding sensitive government information, CMMC 1.0 also added the requirement of third-party certification for all certification levels.
What Is the CMMC Framework?
The original (2020) version of this model categorized contractors into five levels depending on the cybersecurity measures they have to keep controlled unclassified information (CUI) safe. Now, with CMMC 2.0, there will only be three levels.
The CMMC model combines compliance processes from NIST SP 800-171, NIST SP 800-53, ISO 27032, ISO 27001, and AIA NAS9933. Also, the CMMC model uses compliance procedures taken from the Federal Information Security Management Act (FISMA).
The Three Levels of CMMC 2.0 Cybersecurity
The CMMC framework is based on a tiered system that determines the cybersecurity maturity of contractors using three cyber hygiene levels. Each level builds on the last, and all DoD contractors and subcontractors are required to be at least Level 1 certified if they want to move up to the succeeding levels. Below is a breakdown showing the previous five CMMC levels next to the new CMMC 2.0 three-level maturity structure.
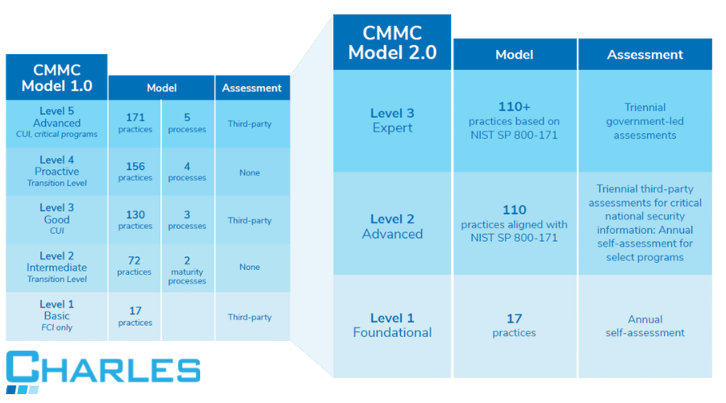
Level 1: Foundational Cyber Maturity
Guided by the Federal Acquisition Regulation (FAR), this is the minimum level of cyber hygiene required to hold Federal Contract Information (FCI), beyond the DoD. A level 1
certification indicates that cybersecurity best practices concerning the identified controls are
“performed” and included in the business’s processes.
This is the easiest of the three levels to achieve, and contractors may self-certify. If you're thinking that CMMC 2.0 Level 1 certification may be right for your business, understand that compliance at this level means you won't meet the full DFARS compliance standards.
Level 2: Advanced Cyber Maturity
Level 2 introduces CUI, a data type that requires safeguarding and disseminating controls. At this level, contractors and subcontractors are required to document the cybersecurity policies and practices for protecting CUI that they have in place. Level 2 is fully aligned with the 14 levels and 110 security controls details in that NIST SP 800-171 Rev. 2 requirements, which include:
- Access control
- Awareness and training
- Audit and accountability
- Configuration management
- Identification and authentication
- Incidence response
- Maintenance
- Media protection
- Physical protection
- Personnel Security
- Risk assessment
- Security assessment
- System and communications protection
- System and information integrity
If your company is working with CUI, you should be aiming for this level of CMMC 2.0 certification.
Level 3: Expert Cyber Maturity
Contractors at this level are required to focus on reducing the risk from Advanced Persistent
Threats (APTs). If you're working with CUI on DoD’s highest priority programs, then this is the CMMC 2.0 level you need to achieve.
The DoD has indicated that its requirements will be based on NIST SP 800-171’s 110 controls plus a subset of NIST SP 800-172 controls. If you have a triennial government-led assessment scheduled, ensure that these are met beforehand to ensure you remain compliant under the new configuration.
As a DoD contractor, you should identify your organization’s cyber security level based on the classification of the data you store, transmit, and process. Your IT team must be famliar with NIST SP 800-171 and the appropriate target levels so that they can determine the right CMMC 2.0 controls to adopt for your organization.
Although the DoD is still developing the requirements for this level, understanding how you can prepare the transition to CMMC 2.0 compliance is a must.
Who Needs to Comply with CMMC?
All contractors and subcontractors are required to have a CMMC certification before they can work on DoD contracts. Noncompliant contractors and subcontractors will be given a stop-work order until they can implement the cybersecurity measures necessary to protect sensitive government information. The DoD can also impose fines and penalties on contractors who make false claims about their certification level and bar them from bidding on future contracts.
How to Prepare for a CMMC Compliance Audit
If you're looking to achieve CMMC 2.0 Level 1 Certification, you'll be able to self certify. However, for levels two and three, contractors are required to undergo an assessment performed by a certified third-party assessor organization (C3PAO).
Here are some tips on how to prepare for a CMMC audit:
- Define CUI specific to your contract(s).
The first step is to indicate your company's CUI environment.
- Perform a self-assessment.
.png?width=245&height=163&name=Call%20Us%20-%20Ryan%20(1).png)
Before the actual audit, DoD contractors can conduct a self-assessment to identify gaps and weak points in their cybersecurity program.
You can do this either in house or outsource the task to a CMMC consultant like Charles IT.
- Conduct a Gap and Readiness Assessment
The next step is to conduct a thorough gap and readiness assessment. This assessment should answer the following questions:
- How is sensitive data stored?
- How is access to that data controlled?
- Is there an effective incident response plan in place?
- Are IT personnel and other staff members adequately trained?
- How are cybersecurity measures implemented and monitored?
If your company is applying for a CMMC certification, you'll need a managed IT services provider (MSP) like Charles IT. Our gap assessment will identify weak spots in your company's IT infrastructure. We will then develop a remediation plan that will help your company achieve CMMC 2.0 compliance. Get a gap assessment today.
Editor's Note: This post was originally published in August 2020, and has been updated to reflect the new CMMC 2.0 requirements.

.png)



