
Endpoint encryption is the process of protecting data stored on endpoints, such as laptops, desktops, tablets, and smartphones. It uses encryption algorithms to scramble the data so that it cannot be read without the decryption key.
In today's increasingly connected world, businesses are more vulnerable than ever to cyberattacks. One of the most effective ways to protect sensitive data from unauthorized access is to implement endpoint encryption.
ever to cyberattacks. One of the most effective ways to protect sensitive data from unauthorized access is to implement endpoint encryption.
There are two main types of endpoint encryption: full disk encryption (FDE) and file-level encryption (FLE). FDE encrypts all of the data on a device, while FLE only encrypts specific files or folders.
How does endpoint encryption work?
Endpoint encryption works by using encryption algorithms to scramble your data. This makes it very difficult for unauthorized users to read your data, even if they have physical access to your device.
data. This makes it very difficult for unauthorized users to read your data, even if they have physical access to your device.
When you encrypt your data, you create a key that is used to scramble the data. This key is then stored on your device. When you want to access your data, you need to enter the key. The key is then used to unscramble the data so that you can read it.
Endpoint encryption offers a number of benefits for businesses, including:
- Increased data security: Endpoint encryption makes it much more difficult for unauthorized users to access sensitive data, even if they steal a device.
- Compliance with regulations: Many industries, such as healthcare and finance, are required to comply with regulations that mandate the use of encryption.
- Reduced IT costs: Endpoint encryption can help to reduce IT costs by reducing the need for data backup and recovery.
There are a number of challenges associated with endpoint encryption, including:
- Complexity: Endpoint encryption can be complex to implement and manage, especially in large organizations.
- Performance: Endpoint encryption can have a negative impact on device performance, especially on older devices.
- User acceptance: Some users may resist using endpoint encryption because it can make it more difficult to access their data.
Despite the challenges, endpoint encryption is a critical security measure that all businesses should consider implementing. By encrypting their endpoints, businesses can significantly reduce the risk of data breaches and protect their sensitive data from unauthorized access.
Here are some additional tips for implementing endpoint encryption: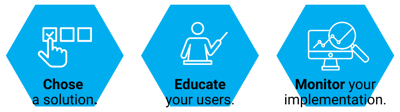
- Choose the right encryption solution: There are a number of different endpoint encryption solutions available, so it is important to choose one that is right for your organization.
- Educate your users: Make sure your users understand the importance of endpoint encryption and how to use it.
- Monitor your implementation: It is important to monitor your endpoint encryption implementation to ensure that it is working properly.
By following these tips, you can ensure that your endpoint encryption implementation is successful and that your sensitive data is protected.
Endpoint encryption is an essential part of any organization's data security strategy. It can help to protect your data from a variety of threats, including theft, loss, and unauthorized access. If you are not already using endpoint encryption, get started today by contacting us!




