
Keeping up with the constantly evolving compliance landscape can be demanding, especially if you’re relying entirely fully on in-house resources to conduct IT security assessments. That said, it’s important to view compliance not as a burden but as a competitive advantage that can earn you more lucrative contracts and help to retain existing ones.
SOC 1 compliance was developed with accounting firms in mind to standardize internal controls over financial reporting (ICFR). Building on that, SOC 2 also revolves around trust service principles and has become necessary for any service provider that stores or transmits customer data. Still, both are important audits in today's age of cloud computing.
Service Organization Controls (SOC)
SOC stands for service organization controls and focuses on those internal controls that are necessary for an audit.
It's easy to confuse the two types of audits because both frameworks were developed by the American Institute of Certified Public Accountants (AICPA) to verify the various technical controls and policies. While their foundations are both based on service organization controls, they differ in terms of focus.
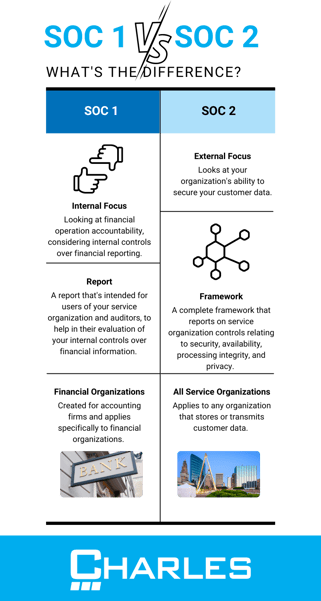
Each SOC audit has a different focus. SOC 1 considers internal control over financial reporting, while SOC 2 considers how you protect customer data. However, both provide critical insight into your technical and operational environment while offering trust and transparency to stakeholders and clients.
 What's the Difference Between SOC 1 and SOC 2?
What's the Difference Between SOC 1 and SOC 2?
As you've just read, the SOC reports differ by focus area. SOC 1 focuses on accountability in financial operations, specifically considering internal control over financial reporting. An evolution of the earlier SAS 70 auditing standards, SOC 1 looks at an organization’s internal control over financial reports to ensure that controls are designed and operating optimally, so they don’t negatively impact financial statements.
In contrast, SOC 2 is a complete framework that turns the focus externally, meaning it looks at how you secure your customer data. Initially introduced in response to the rapid rise in cloud computing, SOC 2 revolves around five key areas known as the Trust Services Criteria:
- Security,
- Availability,
- Processing Integrity,
- Confidentiality, and
- Privacy.
Both SOC 1 and SOC 2 audits come in two forms:
Type 1 focuses on the status of your policies and processes at a given moment in time while Type 2 focuses on how effective those policies are over a given time period (at least six months).
Do I Need a SOC 1 Audit?
If there’s a single word that sums up why you need a SOC 1 audit, it’s trust. Customers are more careful than ever about whom they do business with, and they demand transparency and accountability. Achieving SOC 1 compliance validates your efforts to maintain internal controls over financial reporting to the highest standard.
Almost any service organization can benefit from becoming SOC 1 compliant, despite its origins being with accounting firms and departments. However, SOC 1 is a necessity for service providers in areas like payroll processing and other financial institutions. It’s also a requirement for achieving compliance with the Sarbanes-Oxley Act (SOX).
Do I Need a SOC 2 Audit?
In many ways, SOC 2 has greater reach than SOC 1 since it applies to any company that stores or transmits customer data. As such, it has become necessary for service providers like SaaS businesses and other cloud companies to follow. Even if your organization doesn’t process financial data, it will still need to achieve SOC 2 compliance.
|
Further reading: What is SOC 2 compliance, and why do you need it for your business? |
SOC 2 validates your efforts to protect client data. This goes beyond financial data and includes all personally identifiable data. SOC 2 also requires the implementation of a long-term IT security strategy to protect your systems against new and emerging threats. In addition to security, the SOC 2 framework covers service availability and processing integrity to ensure smooth operations of your critical services.
Now, Do I Also Need a SOC 3 Report?!
You may have heard of the SOC 3 report, which is similar to the SOC 2 report, with the main exception being that it’s designed for general use. SOC 3 reports don’t contain any confidential information about your operational or technical environment, so service firms can use them as marketing collateral to give to their prospective companies.
The IT Security Assessment
Being proactive is key to achieving and maintaining compliance, as well as a high standard of information security and privacy. It all starts with an IT security assessment, which will take a comprehensive view of your security processes and controls and identify potential issues. This will help you continuously improve your security posture and prepare you to pass your SOC audit.
Charles IT provides expert IT security assessments and guidance to ensure your business is ready for the next generation of cyber threats. Book a call today to schedule your assessment!
Editor's Note: This post was originally published in January 2021 and has been updated for accuracy and comprehensiveness.




