
Situation
Older IT Systems and Security Practices Needed a Review
As a full-service supplier of cutting-edge automation and process control systems based in Connecticut, Pearse Bertrum needed to make sure its IT systems and processes were up to date and aligned with current best practices.
They knew some of their hardware was aging and were advised that when equipment or software reaches end-of-life, neither the original manufacturers nor any supporting organizations release further updates. What they didn’t see coming were the ways that outdated equipment and systems would impact IT security.
In addition to these mounting worries, Pearse Bertrum had been experiencing a flood of spam and phishing emails. Each one required careful inspection, draining their employees’ time and attention needed for operations. Problems were stacking up, but without a dedicated IT department, the company was unsure about the best actions to take.
When the time came to find IT help, Wendy Lavoie, Human Resources Manager at Pearse Bertrum, recommended that the leadership team meet with Charles IT. Lavoie recalled the experience she had at a previous company using them as their managed service provider (MSP).
“It was a great working relationship, and they were always responsive,” she says.
Solution
Assess the Problems to Determine Next Steps
Lavoie reached out to Charles IT to start the conversation. After extensive dialogue, Charles IT helped them to see how regular monitoring and managing of equipment and processes were integral to overall IT health. In other words, it wasn’t going to be a matter of simply replacing old hardware and running a few software updates. Pearse Bertrum became aware that processes that had previously met industry standards for IT security needed to be revisited and assessed, and they were ready to get started.
The first step for Charles IT is to listen. Really listen. After a lot of dialogue about Pearse Bertrum’s concerns and existing IT management resources, it became clear that outsourcing the solution made the most sense. They realized they needed a forward-thinking and proactive IT security partner to help in decision-making, IT management, and implementation. Considering how rapidly the modern workplace environment evolves, they also needed help predicting how to address future security and compliance requirements to establish an accurate IT budget.
As with all of Charles IT’s contacts, the first step was to implement an Operational Maturity Level, or OML, assessment. It’s much like the process of renovating a home—you have to look inside the walls and into the foundation before you immediately start making repairs. Otherwise, you risk jumping into “cookie-cutter” solutions that may not make sense for your particular IT environment.
“By conducting the OML, we can really determine whether we're going to be a good fit for each other.” - Jake Forrester, Business Development Expert for Charles IT
The OML is a process whereby Charles IT takes a 360-degree view of a company’s IT environment, closely assessing where that company is vulnerable to security risks. It’s a vital step to start off on the right foot. Forrester explains: “If you want to hire a contractor to renovate your kitchen, it is crucial that your contractor examines the environment prior to offering a quote. The OML assessment acts in the same way; it promotes a better understanding of the work involved in performing necessary tasks.”
During the OML assessment phase, Charles IT expert analysts:
- pinpointed existing vulnerabilities
- isolated potential risks, and
- located areas of opportunity to strengthen Pearse Bertrum’s IT security.
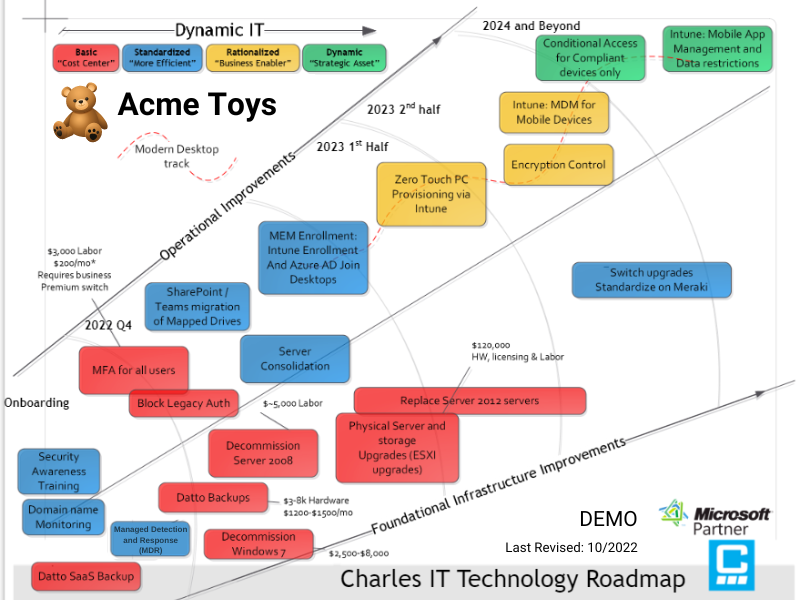
"They identified things that we would need to work on three months from now, six months from now, and a year from now. They had this trajectory diagram that showed the steps to take to get us where we wanted to go, and it was very impressive,” Lavoie says.
These findings represented a shift in paradigm at Pearse Bertrum. Rather than monitor IT systems reactively, Charles IT had provided a better way to address and plan for IT needs.
Sample IT Roadmap
Implementation
A Deep Dive into the IT Environment
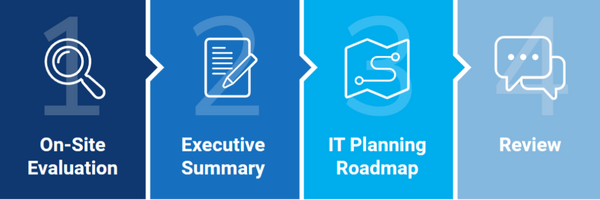
As soon as Pearse Bertrum signed the agreement to begin the OML assessment, Charles IT kicked off their internal project track. After sitting down together to discuss the project expectations and deliverables, Charles IT experts scheduled an on-site visit evaluation, which included running a data collector tool that combed through everything on their network. They also gathered documentation of all IT-related expenses and equipment.
Their expert team went back to the office, combed through all the data, and distilled it into an executive summary. Next, technical solutions engineers reviewed all that information and compiled it into the 22-month IT planning roadmap. This roadmap outlines IT priorities using color-coded criticality designations.
“It was eye-opening. We didn't realize it would be so detailed,” - Wendy Lavoie
Charles IT invited Pearse Bertrum to a review meeting to discuss the results and ask questions about the findings. "The OML assessment definitely showed us that we weren’t where we thought we were with security,” Lavoie says.
Ultimately, the decision to move forward with Charles IT was cemented. “They were happy with what they saw. They asked a bunch of questions about what they wanted more information about, and Foster, our CEO, was able to answer them all. Once they signed the agreement, they were officially set to become a client,” Forrester says.
With the data and insight provided by the OML process, the partnership began with the immediate and most cost-effective solutions already identified.
Results
Efficiency Gains, Reduced Risk, and Accurate Forecasting
There were many valuable takeaways from the OML assessment.
First, Pearse Bertrum identified key system enhancements that needed to take priority. By replacing their outdated server, the company anticipates network speed and overall network enhanced security improvements. Also, by upgrading the phone and internet service, Pearse Bertrum was able to save a substantial amount on monthly expenses.
Security awareness training was introduced for all network users, substantially lowering the risk of hacking and phishing schemes. “While we still get emails like that, they have been curbed by 90 percent,” Lavoie says. With the time saved from managing mountains of phishing emails, Pearse Bertrum employees can focus on the business at hand.
It was also discovered that at some point, someone at Pearse Bertrum had fallen prey to a social engineering scam and inadvertently entered their credentials somewhere they should not have, resulting in their private data being present on the dark web. Charles IT was able to permanently remove these credentials from the dark web, mitigating any further risks. This was an important indicator that Pearse Bertrum could benefit from security awareness training. Their well-meaning employees were in the position of having to discern a legitimate request from a sophisticated social engineering ploy. Charles IT was able to conduct continual training that simulated real-life scenarios whereby an employee may be tempted to give away their data unwittingly. The result? Every employee in the organization was now informed and tested on the latest cybercrime tactics. They knew exactly how to handle those phishing attempts—an important confidence boost that cuts down on wasted time and the risk of a breach.
These examples demonstrate some immediate results and quick wins just a few months into the partnership. However, the real return on investment of the OML assessment only compounds over time. The ability to forecast effectively and identify priorities allows for better allocation of Pearse Bertrum’s resources; It’s a more intentional approach to IT security.
“The OML assessment was a pretty big investment but being in the place where we weren't sure where we stood technologically, it was imperative that we had access to an MSP that was proficient and could translate the terms for others in our company who lack this specialized knowledge,” Lavoie says.
“We are able to trust that Charles IT is on our side." - Wendy Lavoie
Interested in learning more about our OML Assessment and partnership process? Give us a call or schedule a meeting with Jake, today!





