If you’re a Department of Defense (DoD) contractor or a subcontractor dealing with somebody who sells to the DoD, you've probably heard about the Cybersecurity Maturity Model Certification (CMMC). If not, then you should know that beginning in late 2020, the Defense Federal Acquisition Regulation Supplement (DFARS), which regulates how DoD contractors should handle certain types of information on their systems, began to be supplemented by CMMC. Fast forward to November of 2021, when the DoD announced changes to these regulations and described them as enhancements in CMMC 2.0.
Cybersecurity Maturity Model: What is it?
The maturity model concept lays out a series of stages or levels for a certain capability or competence. Higher levels indicate greater capabilities and security. This model makes it explicitly clear what’s required for each level of maturity, from current competencies to organizational processes. CMMC follows this concept, where a contractor’s cybersecurity capabilities are evaluated based on a number of controls and requirements.
CMMC 2.0 addresses the concerns that small and medium-sized businesses (SMBs) were set at a disadvantage since they didn't have the internal IT staff and information security experts that larger companies have. It creates a tiered approach that features three levels of certification that build upon one another.
What are the three levels of the CMMC 2.0 model?
Related article: Know The Difference Between DFARS and CMMC
CMMC Level 1: Foundational Cyber Maturity
There are 17 security controls evaluated at this level. Guided by the Federal Acquisition Regulation (FAR), this is the minimum level of cyber hygiene required to hold Federal Contract Information (FCI), beyond even just the DoD. A level 1 certification indicates that cybersecurity best practices concerning the identified controls are “performed” and included in the business’s processes.
CMMC 1.0 had five levels to achieve, and contractors could self-certify.
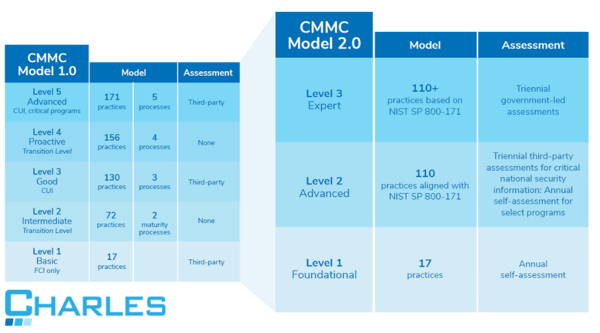
CMMC Level 2: Advanced Cyber Maturity
In addition to fulfilling all Level 1 requirements, contractors are required to be in complete alignment with NIST SP 800-171 practices. This level is designed to align with the 14 levels and 110 security controls set by the National Institute of Technology and Standards (NIST) to protect CUI. Level 2 is now the minimum level required to handle CUI, and most DoD contractors should aim to certify at this level.
Contractors will be required to complete annual self-assessments for selected programs and will need to undergo a triennial third-party assessment for critical national security information.
CMMC Level 3: Expert Cyber Maturity
Contractors who are working with CUI on the DoD's highest priority programs will need to be Level 3 compliant. Compared to the previous CMMC model, this would be the equivalent of level five, where the emphasis is placed on reducing the risk from Advanced Persistent Threats (APTs). In addition to complying with all the requirements of Level 2, contractors will also need to follow a subset of NIST 800-172 controls.
To achieve Level 3 CMMC 2.0 compliance, contractors will need to undergo triennial government-led assessments. Keep in mind, the DoD is still developing the requirements associated with this level, so there may be additional changes announced in 2024.
Preparing for your Cybersecurity Maturity Model Certification
Each cybersecurity maturity level has requirements that all contractors wishing to win a bid for, or keep their current, DoD contract should know in full. While successfully achieving CMMC 2.0 compliance to CMMC is a lot of work, it is possible. There is a wealth of information about CMMC and how to prepare for it, so you can be confident that you'll be able to achieve the certification level you need. To help prepare your business for your CMMC audit, here are some tips from our team.
Knowledge is Power (But Actually...)
You’ll want to start off by learning about the CMMC 2.0 levels and their requirements. By reading this resource and others like it, you’re already ahead of many potential competitors.
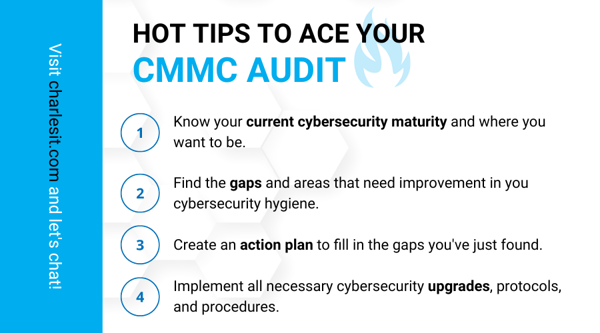
Analyze Your Current Situation
You want to take the next step from reading and learning the CMMC model to identifying where the gaps are between your current cybersecurity maturity and the CMMC level you’re trying to achieve. It’s best to do this with a third-party organization with extensive experience in DFARS compliance, as the official audit will be conducted by an independent third-party organization.
Implement Cybersecurity Solutions
You’ll want to implement a range of cybersecurity solutions that will allow you to fill in the gaps you identified in your current cybersecurity maturity. The solutions you’ll need include:
- Backup and Disaster Recovery to minimize downtime;
- Dark Web Monitoring to prevent credentials from falling into the hands of cybercriminals;
- Endpoint Encryption to ensure that all devices in your network are safe from having sensitive information stolen from them;
- External Vulnerability Scanning to be informed of any potential breaches to your network traffic;
- Security Awareness Training to protect your employees from social engineering attacks and to instruct them on how to respond to cybersecurity incidents; and
- Security Information and Event Management (SIEM) to monitor critical infrastructure for security incidents 24/7.
Evaluate Your Preparedness
Once you’ve identified and filled the gaps in your cyber security hygiene, you’ll need to evaluate your preparedness for the audit. Sooner or later, you’ll confront the question, “Is preparing for the CMMC audit something I am able to do in-house, or should I seek out the help of an expert?” The decision you make should be based on your ability to navigate through the intricacies of this new system. Do you have staff that’s knowledgeable of the CMMC requirements? Are you able to put the required cybersecurity solutions in place on your own? If your answer to these questions is not an immediate yes, then you should consider consulting with an expert.
A gap assessment from a refutable expert in DFARS compliance like Charles IT will not only save you lots of time but also increase your chances of acing your CMMC audit. Contact us now to start filling the gaps in your cybersecurity capabilities!
Editor's Note: This post was originally published in August 2020, and has been updated to reflect the new CMMC 2.0 requirements.

.png)



