
Encryption is the process of converting data into a format that cannot be read without the proper decryption key. It is a critical security measure for protecting sensitive data from unauthorized access, both at rest and in transit.
Encryption is especially important for organizations that must comply with industry regulations, such as HIPAA, CMMC, SOC 2, NIST, and SEC. These regulations require organizations to implement specific security measures to protect sensitive data, including encryption.
Encryption is also important for organizations that purchase cyber insurance. Cyber insurers often require organizations to have certain security measures in place, such as encryption, in order to be eligible for coverage.
Encryption and Compliance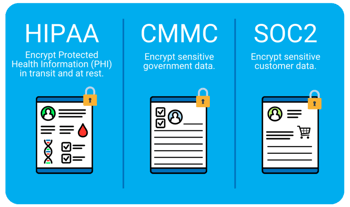
Many industry regulations require organizations to encrypt sensitive data. For example, HIPAA requires organizations to encrypt PHI (protected health information) at rest and in transit. CMMC requires organizations to encrypt sensitive government data, and SOC 2 requires organizations to encrypt sensitive customer data.
Organizations that fail to comply with these regulations may face significant penalties, including fines, reputational damage, and even legal action.
Encryption and Cyber Insurance
Cyber insurers often require organizations to have certain security measures in place, such as encryption, in order to be eligible for coverage. This is because encryption can help to prevent data breaches, which are a major cause of cyber insurance claims.
Organizations that do not have encryption in place may face higher cyber insurance premiums, or even be denied coverage altogether.
Benefits of Endpoint Encryption
Endpoint encryption is the encryption of data on devices such as laptops, desktops, and mobile devices. It is one of the most effective ways to protect sensitive data from unauthorized access.
Endpoint encryption offers a number of benefits, including:
- Compliance: Endpoint encryption can help organizations to comply with industry regulations that require the encryption of sensitive data.
- Data protection: Endpoint encryption can help to protect sensitive data from unauthorized access, even if the device is lost or stolen.
- Reduced risk of data breaches: Endpoint encryption can help to reduce the risk of data breaches, which can be costly and damaging to organizations.
- Eligibility for cyber insurance: Endpoint encryption is often required by cyber insurers in order to be eligible for coverage.
Endpoint Encryption and Specific Industry Regulations
Here is a more detailed look at how endpoint encryption can help organizations to comply with specific industry regulations:
HIPAA
In order to meet HIPAA requirements, organizations must ensure that PHI is encrypted both at rest and in transit. Endpoint encryption is a valuable tool that organizations can utilize to fulfill this requirement by encrypting PHI on various devices, such as laptops, desktops, and mobile devices.
CMMC.png?width=350&height=293&name=Add%20to%20cmmc%20section%20(1).png)
CMMC mandates that organizations must implement encryption measures to safeguard sensitive government data. Endpoint encryption serves as a valuable solution for organizations seeking to meet this requirement by encrypting government data on various devices, including laptops, desktops, and mobile devices.
SOC 2
To meet the suggested requirements of SOC 2, organizations must ensure that sensitive customer data is encrypted. Endpoint encryption provides a valuable solution for complying with this requirement by encrypting customer data on various devices, including laptops, desktops, and mobile devices.
NIST
NIST 800-53 provides a comprehensive framework of security controls that organizations can adopt to safeguard their information systems. A significant number of these controls necessitate the encryption of sensitive data. By implementing endpoint encryption, organizations can effectively meet these requirements and ensure the protection of their valuable information.
SEC
To ensure the protection of their data, organizations involved in securities trading must adhere to security measures mandated by the SEC. Encryption is a key requirement set by the SEC, and implementing endpoint encryption can propel organizations in meeting these obligations.
Endpoint Encryption and Cyber Insurance
As mentioned above, cyber insurers often require organizations to have certain security measures in place, such as endpoint encryption, in order to be eligible for coverage. This is because encryption can help to prevent data breaches, which are a major cause of cyber insurance claims.
Organizations that do not have endpoint in place may face higher cyber insurance premiums, or even be denied coverage altogether.
How to Implement Endpoint Encryption
There are a number of different ways to implement endpoint encryption. One common approach is to use a full disk encryption solution. Full disk encryption encrypts all of the data on a device, including the operating system and applications.
Another approach is to use a file-level encryption solution. File-level encryption encrypts individual files and folders.
The best approach for a particular organization will depend on a number of factors, such as the type of data that needs to be protected, the budget available, and the level of expertise of the IT staff.
HIPAA IT Security
HIPAA IT security is the practice of protecting electronic protected health information (ePHI) from unauthorized access, use, disclosure, disruption, modification, or destruction. HIPAA IT security is important because it helps to protect the privacy and security of patients' health information.
Endpoint encryption is a critical component of HIPAA IT security. By encrypting ePHI on devices such as laptops, desktops, and mobile devices, organizations can help to protect ePHI from unauthorized access, even if the device is lost or stolen.
In addition to endpoint encryption, there are a number of other HIPAA IT security requirements that organizations must comply with. These requirements include:
- Implementing administrative safeguards to protect ePHI, such as policies and procedures for handling ePHI and training employees on HIPAA IT security.
- Implementing physical safeguards to protect ePHI, such as access controls and security cameras.
- Implementing technical safeguards to protect ePHI, such as firewalls, intrusion detection systems, and antivirus software.
IT Security Compliance
IT security compliance is the process of ensuring that an organization's IT systems and data are protected from unauthorized access, use, disclosure, disruption, modification, or destruction. IT security compliance is important because it helps to protect organizations from a variety of cyber threats, such as data breaches, malware attacks, and ransomware attacks.
Endpoint encryption is a critical component of IT security compliance. By encrypting sensitive data on devices such as laptops, desktops, and mobile devices, organizations can help to protect their data from unauthorized access, even if the device is lost or stolen.
In addition to endpoint encryption, there are a number of other IT security compliance requirements that organizations must comply with. These requirements vary depending on the industry and the specific regulations that apply to the organization. However, some common IT security compliance requirements include:
- Implementing a risk assessment process to identify and mitigate security risks.
- Implementing security controls to protect systems and data from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Monitoring systems and data for security threats.
- Responding to security incidents in a timely and effective manner.
IT Security Audit
An IT security audit is an assessment of an organization's IT security posture. IT security audits can be performed internally or by a third-party auditor.
IT security audits typically involve the following steps:
- Planning: The auditor will meet with the organization's management to understand the organization's IT environment and security goals.
- Risk assessment: The auditor will identify and assess the organization's IT security risks.
- Testing: The auditor will test the organization's security controls to determine their effectiveness.
- Reporting: The auditor will prepare a report that includes the findings of the audit and recommendations for improvement.
Endpoint encryption is often one of the areas that is assessed during an IT security audit. The auditor will want to ensure that the organization has implemented effective endpoint encryption controls to protect its sensitive data.
Cybersecurity Business
The cybersecurity business is a growing industry as organizations increasingly invest in protecting their systems and data from cyber threats. The cybersecurity business includes a variety of companies that provide cybersecurity products and services, such as endpoint encryption solutions, firewalls, intrusion detection systems, and antivirus software. Charles IT is one company that specializes in IT and cybersecurity, especially when it comes to organizations with compliance requirements.
Endpoint encryption is a critical component of the cybersecurity business. Endpoint encryption solutions are used by organizations of all sizes to protect their sensitive data from unauthorized access.
The cybersecurity business is expected to continue to grow in the coming years as organizations continue to face new and evolving cyber threats.
Wrapping Up
Endpoint encryption is a critical security measure for protecting sensitive data from unauthorized access. It is especially important for organizations that must comply with industry regulations, such as HIPAA, or that purchase cyber insurance.
There are a number of different ways to implement endpoint encryption, and the best approach for a particular organization will depend on a number of factors. Organizations should carefully consider their needs when choosing an endpoint encryption solution. They should also make sure to implement and maintain their endpoint encryption solution properly. If you're looking for assistance with encryption implementation and/or maintenance, reach out to Charles IT today to see how we can help!




