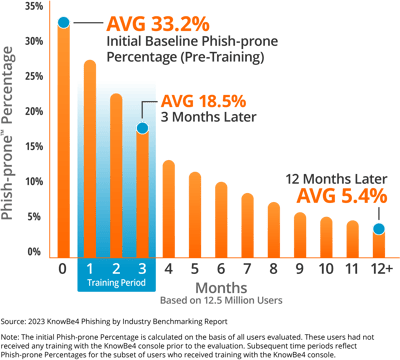
Ensuring employee security awareness and training is crucial for any organization's cybersecurity strategy. By equipping employees with the knowledge to identify and prevent cyberattacks, organizations can effectively safeguard their valuable data and systems from the threats posed by malicious actors.
Why Employee Security Awareness is Essential
In today's digital age, employees play a critical role in an organization's cybersecurity defenses. However, they can also be the weakest link, inadvertently exposing the organization to cyber threats. By equipping employees with the knowledge and skills to identify and avoid cyberattacks, organizations can significantly reduce this risk. Employee awareness training is a powerful tool that empowers employees to become the first line of defense against malicious actors.
Common Cybersecurity Threats
There are many different types of cybersecurity threats, but some of the most common include:
Phishing
Phishing, a notorious cyberattack technique, entails sending deceptive emails or text messages that masquerade as legitimate sources. These misleading messages usually contain enticing links or attachments that, once clicked, unleash malicious software onto unsuspecting victims' computers.
Social engineering
Social engineering is a cunning cyberattack technique that exploits the human element. By manipulating individuals through psychological tactics, social engineers trick victims into divulging personal information or falling for malicious links. These cyber criminals are skilled in the art of manipulation, using various tactics to deceive and exploit their targets.
Malware
Malware is malicious software that can damage or disable a computer system. Malware can be spread through email attachments, infected websites, or removable media.
Ransomware
Ransomware is a type of malware that encrypts a victim's data and then demands payment in exchange for the decryption key.
Zero-day attacks
Zero-day attacks are cyberattacks that exploit vulnerabilities that are unknown to software vendors. Zero-day attacks are often very difficult to defend against.
Employee Awareness Training Topics
Employee awareness training should encompass a diverse array of subjects, ensuring that employees are equipped with the necessary knowledge and skills to combat cyber threats effectively.
- Phishing identification and avoidance
- Social engineering techniques
- Malware prevention
- Ransomware awareness and response
- Zero-day attack prevention
- Password security
- Physical security
- Data protection
- Incident response
Best Practices for Employee Awareness Training
Employee awareness training should be ongoing and regularly updated to reflect the latest threats. Training should be delivered in a variety of formats, such as online courses, in-person training sessions, and simulations. Training should also be tailored to the specific needs of the organization and its employees.
Here are some additional best practices for employee awareness training:
- Make training interactive and engaging.
- Use real-world examples to illustrate the risks and consequences of cyberattacks.
- Encourage employees to ask questions and share their concerns.
- Provide employees with resources and support to help them stay safe
 online.
online.
Consulting with a Managed Service Provider
A managed service provider (MSP) can help organizations to develop and implement an effective employee awareness training program. MSPs have the expertise and experience to help organizations identify the specific risks they face and to develop training programs that are tailored to their needs.
Additional Information
Here is some additional information on some of the topics covered in this blog post:
Phishing
Phishing is one of the most common types of cyberattacks. Phishing emails are designed to trick the recipient into clicking on a malicious link or opening an infected attachment. Phishing emails can be very convincing, and even experienced users can be fooled.
Here are some tips to help you identify phishing emails:
- Be wary of emails from unknown senders.
- Do not click on links or open attachments in emails from unknown senders.
- Hover over links to see the actual URL before clicking on them.
- Look for typos and grammatical errors in emails.
- Be suspicious of emails that ask for personal information, such as your Social Security number or credit card number.
Social Engineering
Social engineering is a type of cyberattack that involves tricking the victim into giving up their personal information or clicking on a malicious link. Social engineers often use psychological techniques to manipulate their victims into doing what they want.
Here are some tips to help you protect yourself from social engineering attacks:
- Be wary of strangers who ask for personal information.
- Do not give out personal information over the phone unless you are sure you are speaking to a legitimate representative of a company or organization.
- Be suspicious of unsolicited phone calls and emails.
- Do not click on links in emails or text messages from unknown senders.
Password Security
Here are some tips to help you create strong passwords:
- Use a password manager to generate and store strong passwords for all of your online accounts.
- Change your passwords regularly, especially if you suspect that your account may have been compromised.
- Do not use the same password for multiple accounts.
Physical Security
Physical security is also important for protecting your data and systems from cyberattacks. Here are some tips for good physical security practices:
- Keep your devices locked and secure when you are not using them.
- Be careful about who you give access to your devices and systems.
- Keep your devices and systems up to date with the latest security patches.
Data Protection
Data protection is the process of protecting your data from unauthorized access, use, disclosure, disruption, modification, or destruction. There are many different ways to protect your data, including:
- Using encryption to protect your data from unauthorized access.
- Implementing access controls to restrict who can access your data.
- Backing up your data regularly to prevent data loss.
Incident Response
Despite your best efforts, cyberattacks can still happen. If you are the victim of a cyberattack, it is important to have a plan in place for responding to the incident. Your incident response plan should include steps for:
- Containing the attack and preventing further damage.
- Investigating the attack to determine how it happened and what data was affected.
- Eradicating the malware from your systems.
- Restoring your data from backup.
- Reporting the attack to the appropriate authorities.
Employee awareness training is an essential part of any organization's cybersecurity strategy. By training employees on how to identify and avoid cyberattacks, organizations can help to protect their data and systems from malicious actors.
One of the most important portions of security awareness training is ensuring that employees stay on top of their trainings. Whether you set them annually, bi-annually, or quarterly, cyber threats are always evolving and keeping your team up to date is the best defense. If you're looking for assistance in implementing and managing your security awareness training, reach out to Charles IT today to see how we can help!