Companies that manufacture products for the US Department of Defense (DoD) must comply with cybersecurity standards set by the Defense Federal Acquisition Regulation Supplement (DFARS). These standards are enforced to ensure that information systems storing contractor data are safeguarded, under the National Institute of Standards and Technology (NIST) Special Publication 800-171 mandate to protect Controlled Unclassified Information (CUI).
Why do manufacturing contractors need a DFARS compliance checklist?
Meeting certain security benchmarks may be too much for small manufacturing companies to handle. Failure to comply, however, will result in penalties, contract suspension, or being stripped of the privilege to be a DoD contractor.
Manufacturing companies can use the following tools to assess the integrity and security of their information systems to avoid the consequences:
✓ Checklist 1: DFARS Compliance
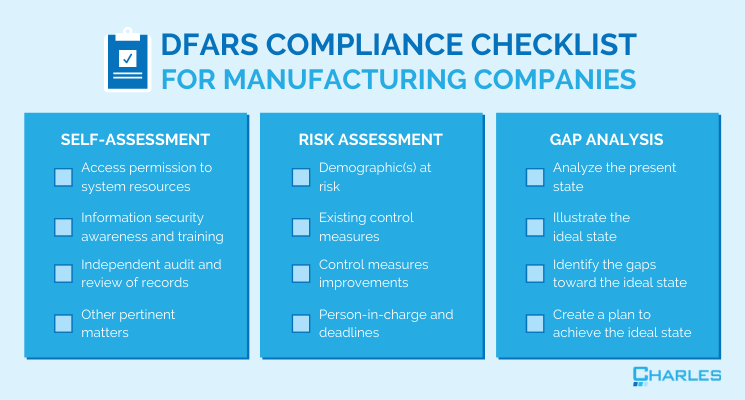
Contractors use the DFARS compliance self-assessment checklist as a tool to assess whether their information systems’ existing security mechanisms adhere to DFARS standards. It contains guidelines that must be followed based on the NIST MEP Cybersecurity Self-Assessment Handbook.
📝 To learn more about DFARS compliance, read our article: Understanding DFARS Compliance: Overview & Requirements.
Using this self-assessment checklist, contractors can examine pertinent compliance matters, including:
- Access permission to system resources – this involves identifying users that can be given access and the type of system resource they’re authorized to use.
- Information security awareness and training – this is aimed at raising users’ and managers’ awareness of the need to protect systems, making employees realize how their actions impact system security, and teaching users correct practices.
- Independent audit and review of records and activities – this is done to establish that operational procedures comply with policies, typically by monitoring system records for unlawful or suspicious activity.
- Other pertinent matters – encompassing information systems maintenance, standard operating procedures implementation in case of security incidents (e.g., malware, natural disasters, corrupted files, etc.), risk assessment about the transmission of CUI, and the like.
To conduct your firm’s DFARS compliance assessment, you may either use in-house resources and expertise or outsource the task to a qualified DFARS consultant that specializes in helping DoD contractors meet compliance rules.
✓ Checklist 2: Risk Assessment
Assessing workplace safety is also one of DFARS’s compliance requirements. DoD contractors can use a risk assessment checklist to manage workplace risks, determine the likelihood of hazards occurring, and implement measures to reduce or eliminate them. Risk assessment depends on factors such as the nature and size of operations and other factors mandated by governing authorities.
In performing a risk assessment, companies must take the following details into account:
- Demographic(s) at risk – this entails identifying which specific groups within the workplace are vulnerable. These could be workers at the assembly line, engineers and technicians, or any other group.
- Existing control measures – having identified the vulnerable demographic(s), you’ll know better how to reduce possible injuries from any workplace risk.
- Control measures improvements – companies must recognize current measures that must be improved or otherwise replaced with more effective measures.
- Person-in-charge and deadlines – to promote accountability in the organization, a person must be put in charge of implementing the new risk prevention measures and set deadlines on when these should be enforced.
Regularly conducting risk assessments in your workplace and IT environment is intended to discover and study your systems’ vulnerabilities, including both physical security threats and cyber threats. While some organizations opt to complete these in-house, many choose to hire outside experts to supplement their in-house teams.
✓ Checklist 3: Gap Analysis
A gap analysis tool is deployed to ascertain that system setups meet DFARS rules. This checklist is meant to find gaps that need to be addressed and improved.
To do a gap analysis, you must:
- Analyze the present state – to check whether employees’ performance is at an optimal level.
- Illustrate the ideal state – that is, describe what processes must look like in the future, given the present state.
- Identify gaps – these pertain to the issues that prevent your organization from achieving the ideal state.
- Create a comprehensive plan – this involves outlining the steps that must be taken to address gaps and setting a deadline for closing them.
For DoD contractors, ensuring adequate information systems security is non-negotiable. Fortunately, defense contractors in Connecticut can work with a knowledgeable managed IT services provider (MSP) such as Charles IT to ensure defense contract compliance. Ticking all the boxes in these checklists can be challenging, so reach out to our team today and be on your way to DFARS compliance!
Editor's Note: This blog was originally published in July 2020 and has been updated for accuracy and relevancy.

.png)